What Windows Application Stores Events Logged By The Operating System
Holbox
Mar 15, 2025 · 6 min read
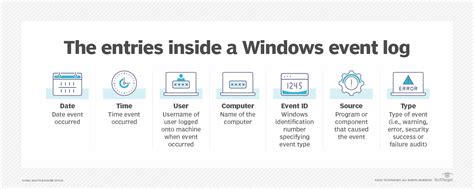
Table of Contents
What Windows Application Stores Events Logged by the Operating System?
The Windows operating system meticulously records a vast array of events, from successful logins to application crashes, hardware changes, and security breaches. Understanding where these events are stored and how to access them is crucial for troubleshooting, security auditing, and system administration. This comprehensive guide will explore the Windows Event Log, its various components, and how to effectively utilize its powerful capabilities.
Understanding the Windows Event Log
The heart of Windows event logging lies within the Event Viewer, a system tool that provides a centralized interface to view and manage logs from various sources. These logs, collectively known as the Windows Event Log, are essentially databases containing structured records of system events. Each event entry includes essential details such as:
- Event ID: A unique numerical identifier for the specific type of event.
- Event Source: The component or application that generated the event.
- Event Type: Categorizes the event (e.g., Error, Warning, Information, Success Audit, Failure Audit).
- Timestamp: The date and time the event occurred.
- User: The user account associated with the event (if applicable).
- Computer: The computer on which the event occurred.
- Description: A detailed explanation of the event.
Locating and Accessing the Event Viewer
Accessing the Event Viewer is straightforward:
- Search: Type "Event Viewer" in the Windows search bar and select the corresponding application.
- Control Panel (Older Versions): Navigate to Administrative Tools and then double-click Event Viewer.
The Event Viewer's interface presents a hierarchical structure, allowing you to explore different logs based on their source.
Key Event Log Components: A Deep Dive
The Event Viewer organizes events into various logs, each serving a specific purpose:
1. Application Log
This log records events related to applications running on the system. It's a crucial resource for troubleshooting application-specific problems. Errors, warnings, and informational messages from applications are logged here. For instance, a failed database connection or an application crash would generate entries in the Application log. Analyzing this log can pinpoint the source of application malfunctions and aid in debugging.
2. System Log
The System log contains events generated by the Windows operating system itself. This is critical for identifying system-level errors, including driver issues, boot failures, hardware problems, and operating system-related problems. Events related to system services, startup processes, and critical operating system functions are found here. Analyzing this log can help diagnose system instability and performance bottlenecks.
3. Security Log
This log is arguably the most crucial for security auditing and incident response. It records security-related events, such as login attempts (successful and failed), access control changes, and security policy modifications. This log provides a detailed audit trail of user activities and system security events, allowing for the detection of malicious activity or security vulnerabilities. Regular review of this log is vital for maintaining system security. Proper configuration is essential – you need to ensure that the necessary security events are being logged and that the log is regularly reviewed and archived.
4. Setup Log
The Setup log, as the name suggests, tracks events related to software installation and uninstallation processes. It records the progress of installations, errors encountered, and completion statuses. This log is valuable for troubleshooting installation issues and verifying successful deployments.
5. Forwarded Events
This log contains events forwarded from other computers in a network environment. Event forwarding is a powerful feature allowing central management and monitoring of multiple computers' event logs in a single location. This is particularly useful for large networks or organizations requiring centralized security monitoring.
6. Custom Logs
Administrators can also create custom logs to track specific events relevant to their applications or systems. This flexibility allows for targeted monitoring of specific processes or applications, enhancing the overall monitoring and troubleshooting capabilities.
Filtering and Searching Event Logs
The sheer volume of events can be overwhelming. Fortunately, the Event Viewer provides powerful filtering and searching capabilities to help you find specific events quickly:
- Filtering: Use the filter options to narrow down the events based on criteria like event type, event source, user, and keywords in the event description. This allows for focused analysis of particular events without getting lost in the vast quantity of entries.
- Searching: The search functionality lets you search for specific event IDs, keywords, or phrases within the event descriptions, providing a targeted approach to locate specific events.
- Custom Views: You can create custom views to save frequently used filters, ensuring efficient access to specific event sets.
Interpreting Event Logs: Practical Examples
Let's consider some practical scenarios to illustrate the importance of understanding event logs:
- Application Crash: If an application crashes repeatedly, checking the Application log for error messages related to that application will provide clues about the cause of the crash. The error messages might indicate issues with specific files, configurations, or dependencies.
- Security Breach Attempt: A failed login attempt would be logged in the Security log, providing critical information for security analysis. By examining the details of the failed attempt, you can identify potential security threats and implement mitigation strategies.
- Hardware Failure: If a hardware component malfunctions, the System log may contain error messages from device drivers or system services related to that hardware. Analyzing these error messages can help diagnose the hardware issue and implement appropriate remedial actions.
- System Performance Degradation: Slowdowns or instability can be traced through the System log, pinpointing issues with services, processes, or driver malfunctions that could be affecting overall system performance.
Beyond the Basics: Advanced Event Log Management
For advanced scenarios, these techniques enhance event log management:
- Event Log Archiving: Regularly archive event logs to maintain a historical record of system events for compliance, auditing, and long-term analysis. Archiving prevents log files from filling up disk space and ensures the persistence of crucial information.
- Centralized Event Log Management: Implement centralized event log management systems for large networks to collect and analyze events from multiple computers in a single location, improving efficiency and providing a holistic view of the network's security and performance.
- Event Log Analysis Tools: Leverage specialized event log analysis tools that can correlate events, identify patterns, and provide advanced insights into system behavior, improving the speed and effectiveness of incident response and troubleshooting.
- Understanding Event ID Numbers: Familiarize yourself with common event ID numbers and their significance. This knowledge allows for more rapid identification and resolution of common issues. Many online resources provide comprehensive event ID number lookups.
Conclusion: Mastering Windows Event Logs for System Health
Mastering the Windows Event Log is a crucial skill for any system administrator, IT professional, or anyone seeking to maintain the health and security of their Windows systems. By understanding the various log components, using filtering and searching effectively, and leveraging advanced management techniques, you can proactively identify and resolve issues, improve security posture, and ensure optimal system performance. The Windows Event Log is not merely a repository of technical details; it's a powerful tool for maintaining system integrity, providing critical insights, and enhancing overall IT operations. Regularly monitoring and analyzing these logs should be a cornerstone of any robust IT strategy.
Latest Posts
Latest Posts
-
Fresh Meat Should Be And Elastic When Pressed
Mar 17, 2025
-
A Preference Decision In Capital Budgeting
Mar 17, 2025
-
If A Company Recognizes Accrued Salary Expense
Mar 17, 2025
-
Utma Accounts Are Opened Under The Tax Id Of The
Mar 17, 2025
-
In Which Situations Can Simplifying Jobs Be Most Beneficial
Mar 17, 2025
Related Post
Thank you for visiting our website which covers about What Windows Application Stores Events Logged By The Operating System . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
