What Is Opsec Select All That Apply
Holbox
Mar 26, 2025 · 7 min read
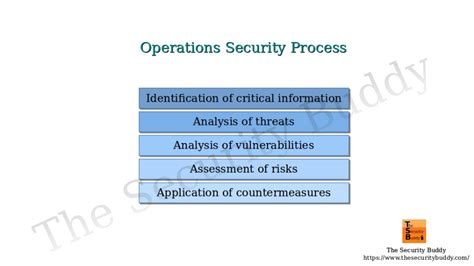
Table of Contents
- What Is Opsec Select All That Apply
- Table of Contents
- What is OPSEC? Select All That Apply
- Understanding the Core Principles of OPSEC
- 1. Identifying Critical Information
- 2. Analyzing Threats
- 3. Identifying Vulnerabilities
- 4. Developing Countermeasures
- 5. Implementing and Monitoring Countermeasures
- OPSEC in Different Contexts
- OPSEC in Business
- OPSEC in Government
- OPSEC in Military Operations
- What is OPSEC? Select All That Apply (Practical Examples)
- The Importance of OPSEC
- Conclusion
- Latest Posts
- Latest Posts
- Related Post
What is OPSEC? Select All That Apply
Operational Security (OPSEC) is a critical process for protecting sensitive information and maintaining a secure operational environment. It's not a single action, but rather a holistic approach encompassing various strategies and techniques. Understanding OPSEC requires a multifaceted perspective, going beyond simple security measures to encompass a proactive and comprehensive approach to risk management. This article will delve deep into the core components of OPSEC, exploring what it entails and providing a detailed explanation to answer the question: "What is OPSEC? Select all that apply."
Understanding the Core Principles of OPSEC
At its heart, OPSEC aims to identify, control, and mitigate risks to sensitive information and operations. This involves a systematic process of analyzing potential threats, identifying vulnerabilities, and developing countermeasures to protect critical assets. The core principles of OPSEC include:
1. Identifying Critical Information
This is the foundational step. Critical information is any data, process, or activity that, if compromised, could significantly harm an organization or individual. This could include:
- Business Plans: Detailed strategies, market analyses, and financial projections.
- Intellectual Property: Patented technologies, trade secrets, and copyrighted materials.
- Personnel Data: Employee information, contact details, and salary information.
- Operational Procedures: Internal processes, workflows, and security protocols.
- Financial Data: Bank account details, transaction records, and investment strategies.
- Customer Data: Personally Identifiable Information (PII), purchasing habits, and preferences.
Identifying this information is paramount. A thorough analysis, possibly involving multiple departments, is crucial for a robust OPSEC strategy.
2. Analyzing Threats
Once critical information is identified, the next step is to analyze potential threats. This involves considering various actors who might try to access or exploit this information, such as:
- Competitors: Seeking to gain a competitive advantage through espionage or intellectual property theft.
- Hackers: Motivated by financial gain, ideology, or simply the thrill of breaching security.
- Foreign Governments: Targeting sensitive information related to national security or economic interests.
- Insider Threats: Malicious or negligent employees who have access to sensitive information.
- Organized Crime: Targeting sensitive financial data for fraudulent activities.
A thorough threat analysis requires considering the capabilities, motivations, and potential actions of each threat actor. This often involves using threat modeling techniques.
3. Identifying Vulnerabilities
This stage focuses on identifying weaknesses in the organization's security posture that could be exploited by threats. These vulnerabilities could include:
- Weak Passwords: Simple passwords easily guessed or cracked.
- Unpatched Software: Outdated software with known security flaws.
- Lack of Encryption: Sensitive data transmitted or stored without encryption.
- Insufficient Access Controls: Inadequate restrictions on who can access sensitive information.
- Physical Security Breaches: Lack of robust physical security measures, like access control to buildings and servers.
- Social Engineering: Weaknesses in employee training that make them susceptible to phishing scams and other social engineering attacks.
- Insider Threats: Unvetted or disaffected personnel who have insider knowledge of systems.
4. Developing Countermeasures
Once vulnerabilities are identified, appropriate countermeasures must be developed and implemented to mitigate the risks. These countermeasures could include:
- Strong Passwords and Multi-Factor Authentication (MFA): Implementing robust password policies and using MFA to add an extra layer of security.
- Regular Software Updates: Ensuring all software is regularly updated to patch security vulnerabilities.
- Data Encryption: Encrypting sensitive data both in transit and at rest.
- Access Control Lists (ACLs): Implementing granular access controls to restrict access to sensitive information.
- Physical Security Measures: Implementing physical security measures such as surveillance cameras, access badges, and security guards.
- Security Awareness Training: Educating employees about security threats and best practices to mitigate social engineering.
- Regular Security Audits: Conducting regular audits to identify and address vulnerabilities.
- Incident Response Plan: Establishing a plan for handling security incidents and breaches.
5. Implementing and Monitoring Countermeasures
The developed countermeasures are not merely planned; they must be implemented and consistently monitored for effectiveness. Regular reviews and adjustments are crucial to ensure the ongoing efficacy of the OPSEC strategy. This may include:
- Regular Security Assessments: Periodically testing the effectiveness of implemented security measures.
- Employee Training and Education: Ensuring employees consistently understand and follow established protocols.
- Incident Reporting and Analysis: Promptly reporting and analyzing any security incidents to learn from mistakes.
- Adaptive Security: Continuously adapting the OPSEC plan to address emerging threats and vulnerabilities.
OPSEC in Different Contexts
The application of OPSEC principles varies depending on the context. Here are some examples:
OPSEC in Business
For businesses, OPSEC involves protecting trade secrets, intellectual property, customer data, and financial information. This can involve implementing strong cybersecurity measures, controlling access to sensitive information, and conducting regular security audits. Consider a startup developing a revolutionary new technology. Their OPSEC would focus heavily on protecting their intellectual property from competitors, using NDAs, secure coding practices, and limiting access to sensitive development information.
OPSEC in Government
Government agencies utilize OPSEC to protect national security information, classified documents, and critical infrastructure. This often involves stricter security protocols, background checks, and access control mechanisms. For example, a defense contractor might use compartmentalized security systems to limit access to sensitive project data based on "need to know" principles.
OPSEC in Military Operations
In military contexts, OPSEC is crucial for protecting troop movements, operational plans, and sensitive intelligence. It involves maintaining secrecy, using secure communications, and implementing deception measures. A military unit planning a covert operation would use OPSEC to ensure enemy forces remain unaware of the time, place, and nature of the operation.
What is OPSEC? Select All That Apply (Practical Examples)
Now, let's answer the initial question with some practical examples. If presented with a multiple-choice question: "What is OPSEC? Select all that apply," the correct answers would include:
- A. Identifying critical information: Knowing which data is most sensitive and needs the highest level of protection is the first step.
- B. Analyzing potential threats: Understanding who might try to access your information and how is crucial.
- C. Implementing security measures: This encompasses all the technical and procedural safeguards put in place.
- D. Regularly reviewing and updating security protocols: OPSEC isn't static; it's a continuous process of adaptation.
- E. Training employees on security awareness: Human error is a significant vulnerability, so educating employees is vital.
- F. Protecting physical assets: This includes securing buildings, servers, and other physical infrastructure.
- G. Using encryption to protect data: Encryption is a cornerstone of data security, protecting information even if intercepted.
- H. Employing strong access controls: Limiting access to sensitive information to only authorized personnel.
- I. Developing an incident response plan: Having a plan in place for handling security breaches is crucial for minimizing damage.
- J. Conducting regular security assessments: Testing the effectiveness of security measures and identifying vulnerabilities.
These options comprehensively illustrate the breadth of OPSEC. It's not just about technology; it's about processes, people, and a proactive approach to risk management.
The Importance of OPSEC
Neglecting OPSEC can lead to serious consequences, including:
- Financial Losses: Data breaches can result in significant financial losses due to theft, fines, and legal costs.
- Reputational Damage: Security breaches can severely damage an organization's reputation and erode public trust.
- Legal Consequences: Failure to protect sensitive information can lead to legal penalties and lawsuits.
- Operational Disruptions: Security incidents can disrupt operations and cause significant delays.
- National Security Risks: In governmental or military contexts, OPSEC failures can compromise national security.
Conclusion
OPSEC is not a one-size-fits-all solution, but a tailored approach that requires continuous evaluation and adaptation. Understanding and implementing a robust OPSEC strategy is vital for any organization or individual handling sensitive information. By proactively identifying threats, vulnerabilities, and critical information, and by consistently implementing and monitoring effective countermeasures, organizations can significantly reduce their risk of security breaches and protect their valuable assets. This holistic approach to security, encompassing technological measures, employee training, and procedural safeguards, is the key to effective OPSEC. Remember that "What is OPSEC? Select all that apply" is a question that demands a broad understanding of this critical security process.
Latest Posts
Latest Posts
-
Draw The Major E2 Reaction Product Formed When Cis 1 Chloro
Mar 29, 2025
-
At A Price Of 15 There Would Be A
Mar 29, 2025
-
Stockholders In A Publicly Held Corporation Have Limited Liability
Mar 29, 2025
-
How Many Variables Are In The Data Set
Mar 29, 2025
-
The Sandwich Approach To Delivering Bad News
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about What Is Opsec Select All That Apply . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
