Packet Tracer - Configuring Extended Acls - Scenario 1
Holbox
Mar 25, 2025 · 6 min read
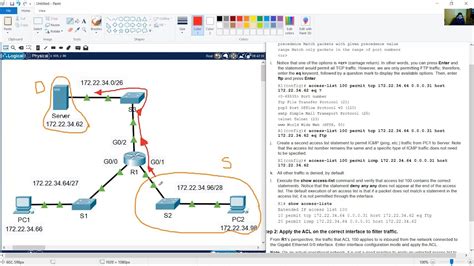
Table of Contents
- Packet Tracer - Configuring Extended Acls - Scenario 1
- Table of Contents
- Packet Tracer: Configuring Extended ACLs - Scenario 1: Securing a Network
- Understanding Extended Access Control Lists (ACLs)
- Why Use Extended ACLs?
- Scenario 1: Securing Internal Network Access
- Step-by-Step Configuration in Packet Tracer
- Advanced Considerations and Best Practices
- Expanding the Scenario: More Realistic Network Security
- Conclusion
- Latest Posts
- Latest Posts
- Related Post
Packet Tracer: Configuring Extended ACLs - Scenario 1: Securing a Network
This comprehensive guide delves into the intricacies of configuring Extended Access Control Lists (ACLs) within Packet Tracer, focusing on a practical scenario designed to enhance your understanding of network security. We'll walk you through the step-by-step process, explaining the rationale behind each configuration choice and highlighting best practices for effective network security implementation.
Understanding Extended Access Control Lists (ACLs)
Before diving into the scenario, let's solidify our understanding of Extended ACLs. These powerful tools allow granular control over network traffic based on various criteria, including:
- Source IP Address: Specifies the IP address or network range of the originating device.
- Destination IP Address: Identifies the IP address or network range of the target device.
- Source Port: Determines the port number used by the originating device.
- Destination Port: Specifies the port number used by the target device.
- Protocol: Defines the network protocol (e.g., TCP, UDP, ICMP).
Extended ACLs provide significantly more precise control compared to Standard ACLs, which only filter based on source IP addresses. This granularity is crucial for implementing robust security policies. They are numbered from 100 to 199.
Why Use Extended ACLs?
Extended ACLs are essential for several reasons:
- Enhanced Security: Precisely control network access, minimizing vulnerabilities.
- Granular Control: Filter traffic based on multiple criteria, enabling sophisticated security policies.
- Improved Network Performance: By blocking unwanted traffic at the network perimeter, they reduce unnecessary network congestion.
- Compliance: Meet regulatory requirements for data security and access control.
Scenario 1: Securing Internal Network Access
Let's imagine a small network with the following devices:
- Router R1: The primary router, responsible for routing traffic between different network segments.
- Server: A web server hosting sensitive data on the 192.168.10.0/24 network.
- Workstations: Several workstations accessing the server and the internet on the 192.168.20.0/24 network.
- Internet: Representing the external network.
Our goal is to configure an Extended ACL on R1 to secure access to the web server. We want to allow only specific workstations to access the server, while denying all other traffic.
Specific Requirements:
- Allow access to the web server (192.168.10.10) only from workstations with IP addresses 192.168.20.10 and 192.168.20.20.
- Deny all other traffic to the web server.
- Allow all other legitimate traffic to flow normally (e.g., internet access for workstations).
Step-by-Step Configuration in Packet Tracer
Here's a detailed walkthrough of the configuration process in Packet Tracer:
-
Access Router R1: Open Packet Tracer and connect to the console of router R1.
-
Enter Configuration Mode: Use the command
configure terminal. -
Create the Extended ACL: We'll use ACL number 110. The command is:
access-list 110 extended permit tcp 192.168.20.10 0.0.0.0 eq 80 192.168.10.10 0.0.0.0 eq 80 access-list 110 extended permit tcp 192.168.20.20 0.0.0.0 eq 80 192.168.10.10 0.0.0.0 eq 80 access-list 110 extended deny ip any anyExplanation:
access-list 110 extended: Defines an extended ACL with the number 110.permit tcp 192.168.20.10 0.0.0.0 eq 80 192.168.10.10 0.0.0.0 eq 80: Allows TCP traffic from workstation 192.168.20.10 to the web server (192.168.10.10) on port 80 (HTTP).0.0.0.0is used as wildcard mask for the host.eq 80specifies the exact port number.permit tcp 192.168.20.20 0.0.0.0 eq 80 192.168.10.10 0.0.0.0 eq 80: Similar to the previous line, but for workstation 192.168.20.20.deny ip any any: This is an implicit deny statement. It denies any other IP traffic not explicitly permitted in the ACL. This is crucial for security; any traffic not explicitly allowed is blocked.
-
Apply the ACL: We need to apply the ACL to the appropriate interface. Let's assume the interface connecting to the 192.168.10.0/24 network is GigabitEthernet0/0.
interface GigabitEthernet0/0 access-group 110 inThis command applies ACL 110 to the inbound traffic on GigabitEthernet0/0.
-
Save the Configuration: Use the command
endto exit configuration mode and thencopy running-config startup-configto save the changes persistently. -
Verification: Use Packet Tracer's simulation capabilities to test the ACL. Try accessing the web server from different workstations. Only workstations 192.168.20.10 and 192.168.20.20 should be able to reach the server. You can use the
show access-listscommand to verify the ACL configuration on the router.
Advanced Considerations and Best Practices
-
Implicit Deny: Always include an implicit deny statement (like
deny ip any any) at the end of your ACL. This ensures that any traffic not explicitly permitted is blocked, providing a critical layer of security. -
Sequence Numbers: Although not mandatory in this scenario, using sequential numbers for your ACL statements improves readability and maintainability, especially in more complex ACLs.
-
Wildcard Masks: Understand how wildcard masks work. They are used to specify the range of IP addresses permitted or denied. For example,
0.0.0.0represents a single IP address, while0.0.0.255represents all addresses in the last octet. -
Port Numbers: Be specific with your port numbers. Using well-known port numbers (e.g., 80 for HTTP, 443 for HTTPS) is crucial for accurately filtering traffic. You can also use keywords like
eq(equal),gt(greater than), andlt(less than) to define port ranges. -
Testing and Monitoring: Thoroughly test your ACL configuration in a controlled environment before deploying it to a production network. Regularly monitor your ACLs for effectiveness and make adjustments as necessary.
-
Logging: Consider enabling logging for ACL events. This allows you to track and analyze traffic that is permitted or denied by the ACL, aiding in security auditing and incident response. This is a crucial step for robust security monitoring.
-
Regular Updates: Network security is a continuous process. Regularly review and update your ACLs to reflect changes in your network topology, applications, and security policies.
Expanding the Scenario: More Realistic Network Security
This scenario provides a fundamental understanding of configuring Extended ACLs. However, real-world network security is often more complex. Consider the following extensions:
-
Multiple Services: Extend the ACL to control access to other services running on the server, such as SSH (port 22), FTP (ports 20 and 21), or other applications.
-
Different Protocols: Include rules for different protocols such as UDP, ICMP, etc., to refine traffic filtering.
-
Network Segmentation: Implement additional ACLs to segment the network further, isolating sensitive resources from less critical parts of the network. This helps to contain security breaches and limit their impact.
-
Named ACLs: Use named ACLs instead of numbered ones to improve readability and management. This is particularly useful in more complex network configurations.
Conclusion
Configuring Extended ACLs is a fundamental skill for network administrators. This comprehensive guide, combined with hands-on practice using Packet Tracer, empowers you to implement robust network security measures. Remember to always prioritize security best practices, conduct thorough testing, and regularly review your ACL configurations to maintain a secure and efficient network environment. Through diligent application of these principles and constant learning, you can successfully secure your network and protect valuable data against unauthorized access and cyber threats. Continue practicing and exploring different scenarios to build your expertise in network security.
Latest Posts
Latest Posts
-
A Wave Having A Frequency Of 1000 Hertz Vibrates At
Mar 29, 2025
-
Match The Following Tooth Structures With Their Functions
Mar 29, 2025
-
To Purchase Insurance The Policyowner Must Face The Possibility
Mar 29, 2025
-
Which Of The Following Is An Oxidation Reduction Reaction
Mar 29, 2025
-
Air At 30000 Feet Is At A Temperature Of
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about Packet Tracer - Configuring Extended Acls - Scenario 1 . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
