Which Of The Following Do Pretexting Scams Often Rely On
Holbox
Mar 18, 2025 · 6 min read
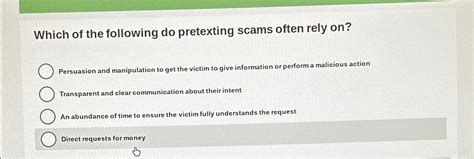
Table of Contents
Which of the Following Do Pretexting Scams Often Rely On? A Deep Dive into Deception
Pretexting scams are a sneaky form of social engineering that rely on deception to gain access to sensitive information. Victims are tricked into revealing personal details, financial data, or login credentials under false pretenses. Understanding the tactics employed in these scams is crucial to protecting yourself and your loved ones. This comprehensive guide explores the various methods pretexting scams often rely on, offering insights into how they operate and strategies to avoid becoming a victim.
The Pillars of Pretexting: Building a Foundation of Deceit
Pretexting scams are successful because they play on human trust and our natural inclination to help. They are carefully crafted scenarios designed to elicit a specific response—the disclosure of valuable information. The success of a pretexting scam hinges on several key pillars:
1. Establishing Credibility and Urgency:
This is the cornerstone of any successful pretexting attack. Scammers will create a believable persona and scenario to gain your trust. They might impersonate:
- Government officials: Claiming to be from the IRS, Social Security Administration, or other government agencies investigating fraudulent activity. They often use threatening language to create urgency.
- Bank representatives: Reporting suspicious activity on your account and requesting verification of your details to "secure" your funds.
- Tech support personnel: Alerting you to a critical system issue requiring immediate attention and remote access to your computer.
- Family members or friends: Creating a believable emergency scenario requiring immediate financial assistance or personal information. This tactic exploits emotional vulnerabilities.
The urgency element is critical. By creating a sense of panic or immediate need, scammers limit the time victims have to think critically and verify the information.
2. Manipulating Emotions:
Pretexting scams exploit human emotions to their advantage. They understand that:
- Fear is a powerful motivator: The threat of legal action, financial loss, or harm to loved ones can easily overwhelm rational thought.
- Empathy can be exploited: Scammers prey on victims' desire to help others, particularly in scenarios involving family or friends in distress.
- Curiosity can be a weakness: Intriguing or unexpected requests can prompt victims to reveal information without fully considering the consequences.
3. Gathering Intelligence:
Before initiating contact, scammers often spend time gathering information about their targets. This “pre-texting” research allows them to tailor their approach for maximum impact. They may use publicly available information or social engineering techniques to:
- Learn your name, address, and other personal details: This allows them to create a more believable and personalized interaction.
- Identify your relationships: This enables them to craft scenarios involving family or friends, making the scam more convincing.
- Discover your financial institutions: This helps them tailor their approach to mimic legitimate communications from banks or other financial institutions.
The more information scammers have, the more effective their deception will be.
Common Tactics Employed in Pretexting Scams
Pretexting scams utilize a variety of tactics to deceive their victims. Here are some of the most common:
1. Phishing:
While often used independently, phishing is a key component of many pretexting scams. Scammers send deceptive emails, text messages, or phone calls containing links to fake websites or requesting sensitive information. These phishing attempts are often highly targeted, leveraging the information gathered during the intelligence-gathering phase.
2. Vishing (Voice Phishing):
Vishing uses phone calls to deceive victims. Scammers may impersonate bank representatives, government officials, or tech support personnel, using convincing voice impersonation techniques to pressure victims into revealing personal information. The urgency and pressure tactics are amplified in vishing scams.
3. Smishing (SMS Phishing):
Smishing uses text messages to deliver deceptive links or requests for information. The short and concise nature of text messages makes them ideal for creating a sense of urgency. Scammers often include shortened URLs or numbers that mask the true destination.
4. Baiting:
This involves offering something desirable (a prize, a discount, or a job opportunity) to lure victims into revealing their personal information. The bait is often too good to be true, encouraging victims to overlook red flags.
5. Quid Pro Quo:
This tactic involves offering something in exchange for information. For example, scammers might offer assistance with a technical problem in exchange for remote access to a victim's computer.
Identifying and Avoiding Pretexting Scams
Protecting yourself from pretexting scams requires a combination of vigilance and critical thinking. Here's how you can safeguard yourself:
1. Verify Information Independently:
Never trust unsolicited calls, emails, or text messages requesting personal information. Always verify the identity of the person or organization contacting you by using a publicly available phone number or website, not the one provided in the suspicious communication.
2. Be Wary of Urgency:
Legitimate organizations rarely demand immediate action. If someone is pressuring you to act quickly, be extremely cautious. Take your time to consider the request and verify the information independently.
3. Don't Share Sensitive Information:
Never share your passwords, social security number, bank account details, or other sensitive information through email, text message, or phone call unless you have initiated the contact and are confident of the recipient's identity.
4. Report Suspicious Activity:
If you suspect you've been targeted by a pretexting scam, report it immediately to the appropriate authorities, such as the Federal Trade Commission (FTC) or your local law enforcement agency. This helps protect others from falling victim to the same scam.
5. Educate Yourself and Others:
Stay informed about the latest pretexting scams and share your knowledge with friends and family. The more people understand these tactics, the less effective they will be.
6. Use Strong Passwords and Multi-Factor Authentication:
Implement strong, unique passwords for all your online accounts and enable multi-factor authentication whenever possible. This adds an extra layer of security, even if your credentials are compromised.
7. Be Skeptical:
Maintain a healthy level of skepticism. Don't be afraid to question requests for information and verify the legitimacy of any communication before responding. If something feels off, it likely is.
The Evolving Landscape of Pretexting: Staying Ahead of the Curve
Pretexting scams are constantly evolving, with scammers employing new techniques to bypass security measures and deceive victims. Staying informed about the latest trends is crucial to protect yourself. Keep an eye on news reports and security advisories to learn about new tactics and strategies employed by scammers. Regularly update your security software and be vigilant about suspicious communications. Remember, your vigilance is your best defense against these sophisticated and persistent attacks.
Conclusion: Proactive Protection is Key
Pretexting scams thrive on exploiting human vulnerabilities. By understanding the techniques employed by scammers and taking proactive steps to protect yourself, you can significantly reduce your risk of becoming a victim. Remember, the key to avoiding these scams is a combination of vigilance, critical thinking, and a healthy dose of skepticism. Stay informed, stay safe, and never hesitate to question anything that feels suspicious.
Latest Posts
Latest Posts
-
The Federal Reserve Sells Government Securities To
Mar 18, 2025
-
The Stomach Is Blank To The Spine
Mar 18, 2025
-
Select The Correct Definition Of A Glycolipid
Mar 18, 2025
-
The First Step In Task Analysis Is To
Mar 18, 2025
-
What Products Are Expected In The Ethoxide Promoted
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Do Pretexting Scams Often Rely On . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
