Which Best Describes The Terrorist Planning Cycle
Holbox
Mar 24, 2025 · 7 min read
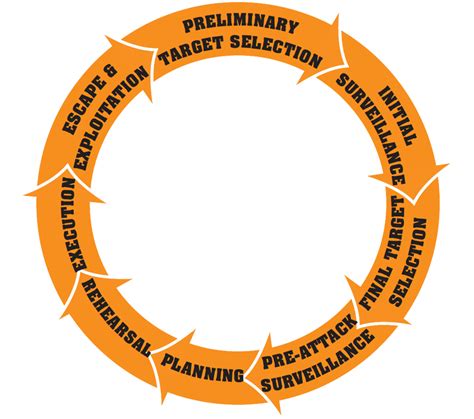
Table of Contents
- Which Best Describes The Terrorist Planning Cycle
- Table of Contents
- Which Best Describes the Terrorist Planning Cycle? A Deep Dive into the Phases of Terrorist Attacks
- Phase 1: Ideation and Target Selection
- Ideological Motivations:
- Grievances and Justifications:
- Target Selection:
- Phase 2: Planning and Preparation
- Reconnaissance:
- Resource Acquisition:
- Team Formation and Roles:
- Rehearsals and Contingency Planning:
- Phase 3: Attack Execution
- Timing and Coordination:
- Methods and Tactics:
- Escape and Evasion:
- Phase 4: Post-Attack Phase
- Claiming Responsibility:
- Assessment and Analysis:
- Recruitment and Reorganization:
- Maintaining Momentum:
- Variations in the Terrorist Planning Cycle:
- Conclusion: Understanding the Cycle for Effective Counter-Terrorism
- Latest Posts
- Latest Posts
- Related Post
Which Best Describes the Terrorist Planning Cycle? A Deep Dive into the Phases of Terrorist Attacks
Terrorism, a scourge on humanity, is not a spontaneous act of violence. It's a meticulously planned operation, often involving multiple individuals and intricate steps. Understanding the terrorist planning cycle is crucial for effective counter-terrorism strategies. While variations exist depending on the group, ideology, and target, a common framework emerges, allowing us to analyze and predict potential attacks. This article delves into the various stages of this cycle, exploring the nuances and complexities involved in each phase.
Phase 1: Ideation and Target Selection
This initial phase is the genesis of the terrorist plot. It involves the conceptualization of the attack, driven by the terrorist group's ideology, grievances, and objectives. This stage isn't always clearly defined; it can be a gradual process of radicalization and escalating commitment.
Ideological Motivations:
The root of most terrorist plots lies in a deeply held ideology. This could range from religious extremism (e.g., Islamic extremism, Christian fundamentalism) to political ideologies (e.g., nationalism, anarchism) or even ethno-nationalist grievances. The group's core beliefs dictate the overall goals, the acceptable means to achieve those goals, and the selection of targets.
Grievances and Justifications:
Terrorist groups often cite grievances—real or perceived injustices—to justify their actions. These grievances might include political oppression, economic inequality, historical injustices, or foreign policy interventions. The framing of these grievances within their ideological lens fuels the desire for violent action.
Target Selection:
Identifying a suitable target is crucial. The selection process considers several factors:
- Symbolic Value: Targets are often chosen for their symbolic importance. Attacking a government building, a religious site, or a cultural landmark sends a powerful message, demonstrating the group's power and highlighting their grievances.
- Vulnerability: Terrorists seek targets that offer minimal security and present a high likelihood of success. Soft targets, such as crowded public spaces, are often preferred over heavily guarded installations.
- Impact: The potential impact of the attack is also a key consideration. The goal is to maximize casualties, damage, and overall disruption, creating fear and influencing public opinion.
- Accessibility: The target's accessibility plays a vital role. The group must be able to reach the target undetected and execute the plan effectively.
Phase 2: Planning and Preparation
Once a target is selected, the detailed planning phase begins. This is a meticulous process involving several sub-phases:
Reconnaissance:
This involves gathering intelligence on the target. Terrorists may conduct physical surveillance, using various techniques to observe security measures, identify vulnerabilities, and map out escape routes. They may also gather information through open-source intelligence (OSINT) – publicly available information – or human intelligence (HUMINT) – information gathered from people.
Resource Acquisition:
This crucial stage involves acquiring the necessary resources for the attack. This might include weapons, explosives, vehicles, communication equipment, and funding. The methods used vary greatly depending on the group's capabilities and resources. Some groups may rely on illicit arms markets, while others might utilize locally sourced materials. Funding is often secured through donations, criminal activities, or external sponsors.
Team Formation and Roles:
Terrorist groups rarely operate alone. The planning phase involves assembling a team with diverse skills and responsibilities. Some members might specialize in reconnaissance, others in explosives, while others handle logistics and communication. Clear roles and responsibilities are essential for the smooth execution of the plan.
Rehearsals and Contingency Planning:
To ensure the success of the attack, rehearsals and contingency planning are essential. This involves practicing the attack sequence, identifying potential challenges, and developing strategies to overcome them. This phase significantly reduces the risk of failure and enhances the group's operational efficiency.
Phase 3: Attack Execution
This is the culmination of the planning process. The execution phase requires precision, coordination, and adherence to the plan. However, even the most meticulously planned attacks can encounter unexpected challenges.
Timing and Coordination:
The choice of timing is critical. Terrorists often select times when security is lax or when the target is most vulnerable. Coordination among team members is essential to ensure the attack proceeds as planned. Communication protocols are vital for keeping everyone informed and reacting to unexpected events.
Methods and Tactics:
The methods used for the attack vary widely, from bombings and shootings to hijackings and cyberattacks. The chosen method depends on the target, resources, and the group's capabilities. Sophistication in attack methods can vary greatly, from simple improvised explosive devices (IEDs) to highly complex and technologically advanced attacks.
Escape and Evasion:
Planning for escape and evasion is a crucial component. This involves establishing escape routes, transportation methods, and potential hiding places. The group needs to minimize the risk of apprehension following the attack. This phase often involves careful consideration of potential law enforcement responses and strategies to evade capture.
Phase 4: Post-Attack Phase
The aftermath of the attack is equally critical for terrorist groups. This phase involves consolidating successes, analyzing failures, and preparing for future operations.
Claiming Responsibility:
Terrorist groups often claim responsibility for their attacks, often using propaganda to promote their ideology, justify their actions, and intimidate the population. This is a significant aspect of achieving their psychological goals, and shaping public perception.
Assessment and Analysis:
After the attack, the group undertakes a thorough assessment of the operation's success or failure. They analyze what went right, what went wrong, and identify areas for improvement in future attacks. This post-operational analysis is invaluable for refining their techniques and improving future operational efficiency.
Recruitment and Reorganization:
The attack's impact can affect recruitment. A successful attack may boost morale and attract new members, while a failure could lead to internal conflicts and reorganization. The group may need to recruit new members to replace those killed or captured, or to reshape its structure following the attack.
Maintaining Momentum:
Following an attack, terrorist organizations often work to capitalize on the event and maintain operational momentum. This may involve intensifying their propaganda campaign, escalating attacks, or shifting tactics to avoid detection. Maintaining the narrative and keeping the public focused on their grievances is a key objective in this phase.
Variations in the Terrorist Planning Cycle:
It's crucial to remember that the terrorist planning cycle is not monolithic. Several factors influence its duration and specifics:
- Group Size and Structure: Larger, more established groups have more resources and a more formalized structure, leading to more complex planning. Smaller groups may have simpler plans with less sophisticated resources.
- Ideology and Objectives: The group's ideology and objectives impact the choice of targets and the level of violence employed. Some groups prioritize symbolic attacks, while others focus on mass casualties.
- Technological Capabilities: Access to technology and expertise can significantly influence the planning process. Sophisticated groups might use advanced communication systems, drones, or other technology to enhance their operations.
- External Support: Access to external funding, training, or weapons can significantly enhance a group's capabilities and influence the complexity of its planning.
Conclusion: Understanding the Cycle for Effective Counter-Terrorism
Comprehending the terrorist planning cycle is paramount for developing effective counter-terrorism strategies. By understanding the different stages, from ideation and target selection to post-attack assessment, security agencies can better predict, prevent, and respond to terrorist attacks. This understanding allows for proactive measures, such as identifying potential threats, disrupting the planning process, and strengthening security measures at vulnerable targets. Continuous monitoring and analysis of terrorist group activities, along with international cooperation and intelligence sharing, remain essential components in combating this global threat. The multifaceted nature of terrorism demands a multifaceted approach to counter it. Successfully disrupting the cycle requires a holistic strategy that addresses the underlying ideological motivations, addresses grievances, and works to prevent the radicalization of individuals. Only through a comprehensive and adaptive approach can we hope to effectively mitigate the threat of terrorism and create a safer and more secure world.
Latest Posts
Latest Posts
-
Report For Experiment 14 Identification Of Selected Anions
Mar 29, 2025
-
Identify The Forces On The Jet
Mar 29, 2025
-
In Consultative Selling The Customer Is Seen As
Mar 29, 2025
-
One Penny At A Time Sams Club Percentage
Mar 29, 2025
-
Regardless Of The Inventory Costing System Used
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about Which Best Describes The Terrorist Planning Cycle . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
