What Are The Two Parts Of A Mac Address Called
Holbox
Mar 10, 2025 · 6 min read
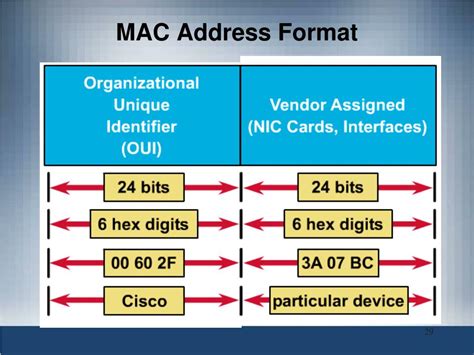
Table of Contents
Decoding the MAC Address: Understanding its Two Key Components
A Media Access Control (MAC) address is a unique identifier assigned to network interfaces for communication on a network segment. While often presented as a single, seemingly monolithic string of alphanumeric characters, a MAC address is actually composed of two distinct parts: the Organizationally Unique Identifier (OUI) and the Device Identifier (Serial Number). Understanding these two components is crucial for network administration, troubleshooting, and security. This comprehensive guide delves deep into each part, exploring their functions, significance, and implications.
Understanding the Organizationally Unique Identifier (OUI)
The OUI, the first 24 bits (three bytes) of a MAC address, identifies the manufacturer of the network interface card (NIC) or other network device. It's essentially a company's unique identification number within the MAC address space, globally administered by the IEEE (Institute of Electrical and Electronics Engineers). Think of it as a company's postal code in the world of network addresses. Each manufacturer is assigned a unique OUI, ensuring that no two manufacturers share the same identifier.
Why is the OUI important?
- Manufacturer Identification: The OUI immediately reveals the manufacturer of the network device. This is vital for network administrators to quickly identify the hardware on their network, facilitating troubleshooting and inventory management.
- Network Security: OUI information can help in security investigations. By identifying the manufacturer, security professionals can better understand the source of malicious activity or unauthorized network access.
- Device Compatibility: In some cases, understanding the OUI can be helpful in determining device compatibility with specific network equipment or software.
- Supply Chain Management: For manufacturers, OUI information is crucial for tracking their products throughout the supply chain.
Where to find OUI information?
The IEEE maintains a publicly accessible database of assigned OUIs. This database allows anyone to look up the manufacturer associated with a specific OUI. This is a valuable resource for network professionals and anyone interested in understanding the origins of network devices. Searching the database is usually straightforward, requiring only the first three bytes (hexadecimal digits) of the MAC address.
OUI examples:
- 00:00:0C: This OUI is assigned to Cisco Systems, Inc.
- 00:16:3E: This OUI is assigned to Dell Inc.
- 00:0C:29: This OUI is assigned to Intel Corporation.
These examples highlight how the initial segment of the MAC address immediately points to the manufacturer. This feature significantly simplifies network identification and management.
Delving into the Device Identifier (Serial Number)
The second part of a MAC address, the Device Identifier (also known as the serial number), is the remaining 24 bits (three bytes) assigned by the manufacturer. This portion is unique to each individual network interface card produced by that manufacturer. It's like a serial number on a product that distinguishes it from other identical products. The manufacturer uses internal processes to assign these serial numbers, ensuring no two devices produced by the same manufacturer have the same MAC address.
The Role of the Device Identifier:
- Uniqueness: The key function is to guarantee uniqueness within the manufacturer's OUI. It ensures that each network interface card has a globally unique MAC address, crucial for preventing address conflicts on a network.
- Inventory Management: The device identifier aids in tracking individual devices produced by a manufacturer. This is particularly important for manufacturers managing large-scale production.
- Troubleshooting: In conjunction with the OUI, the device identifier provides a complete and unique identifier that can aid in troubleshooting network connectivity issues.
Variations in Device Identifier Assignment:
Manufacturers employ different methods for assigning the device identifier. Some manufacturers use sequential numbering, while others may use more complex algorithms to ensure random distribution and prevent predictable patterns that could potentially be exploited for malicious purposes. The specific method employed is an internal matter for each manufacturer.
The Importance of Uniqueness:
The combined OUI and device identifier create the unique MAC address. This global uniqueness is fundamental to the proper functioning of network communications. Without this unique identifier, it would be impossible to distinguish between different devices on a network, leading to collisions and communication failures.
MAC Address Structure: A Closer Look
Let's examine the structure in more detail. A MAC address is typically represented as a 12-digit hexadecimal number, separated into six groups of two digits by colons. For example: 00:16:3E:1A:A3:4D.
This seemingly simple string of characters represents a unique identifier for a network interface, broken down as follows:
- Bytes 0-2 (OUI):
00:16:3EIn this example, this indicates the manufacturer, which, based on the IEEE OUI database, can be identified. - Bytes 3-5 (Device Identifier):
1A:A3:4DThis portion uniquely identifies the specific device within the manufacturer's range.
The combination of these two components ensures global uniqueness, a fundamental requirement for reliable network communication.
Practical Applications and Implications
Understanding the two parts of a MAC address has several practical applications:
- Network Troubleshooting: When network connectivity problems arise, knowing the OUI and device identifier helps narrow down the source of the issue. For instance, you can easily identify if the issue is with the device itself or with the network infrastructure.
- Network Security: MAC address filtering is a security mechanism used to control access to a network. By specifying allowed MAC addresses, you can restrict access to authorized devices.
- Device Management: Network administrators use MAC addresses to inventory devices, track their location, and monitor their activity on the network.
- Forensics: In network security investigations, MAC addresses provide crucial information for tracing the origin of malicious activity.
MAC Address vs. IP Address: Key Differences
It's important to differentiate between MAC addresses and Internet Protocol (IP) addresses. While both are crucial for network communication, they serve different purposes:
- MAC Address: A physically assigned, unique identifier permanently embedded in the network interface card. It’s a local address within a network segment.
- IP Address: A logical address assigned to a device for communication across a network. It’s a globally routable address that can change.
MAC addresses are used for communication within a local network, whereas IP addresses are used for communication across larger networks. The two work in tandem to enable seamless data transfer across various network levels.
Conclusion: The Significance of MAC Address Components
Understanding the two parts of a MAC address – the OUI and the device identifier – is essential for effective network management, security, and troubleshooting. The OUI provides immediate identification of the manufacturer, while the device identifier ensures uniqueness within that manufacturer's product line. This two-part structure is fundamental to the operation of networks worldwide, guaranteeing the seamless and reliable communication that underpins modern digital infrastructure. The information provided in this article empowers network administrators, security professionals, and anyone interested in networking technology to better understand this critical aspect of network functionality and its implications. By grasping the significance of each component, individuals can gain a deeper understanding of how networks function and how to effectively manage and secure them. Furthermore, this knowledge contributes to more efficient troubleshooting and improved network performance.
Latest Posts
Latest Posts
-
When Can A Public Health Inspector Visit An Establishment
Mar 10, 2025
-
Which Wall Needs To Be Stronger 6m Or 3m
Mar 10, 2025
-
When Is Whmis Training Required Check All That Apply
Mar 10, 2025
-
What Formula Would Produce The Value In Cell C25
Mar 10, 2025
-
Four Process Strategies Defniation And Example
Mar 10, 2025
Related Post
Thank you for visiting our website which covers about What Are The Two Parts Of A Mac Address Called . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
