Remote Access May Be Permitted For Privileged Functions
Holbox
Mar 17, 2025 · 6 min read
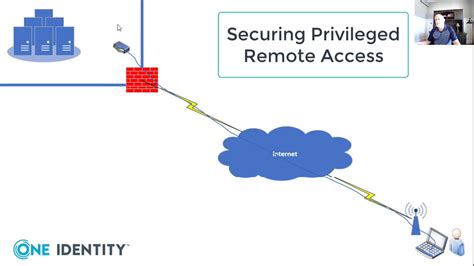
Table of Contents
Remote Access: A Necessary Evil? Permitting Privileged Functions Access
Remote access to systems, especially those with privileged functions, presents a significant security challenge. While it offers undeniable advantages in terms of flexibility and efficiency, it also dramatically expands the attack surface, making organizations vulnerable to a wide range of threats. This article will delve into the complexities of permitting remote access for privileged functions, examining the risks, mitigation strategies, and best practices to ensure a secure and productive environment.
The Allure of Remote Access for Privileged Functions
Privileged functions, by definition, grant extensive control over systems and data. These functions are often crucial for managing infrastructure, troubleshooting issues, and performing essential administrative tasks. Historically, access to these functions was restricted to individuals physically present in the data center. However, the rise of cloud computing, remote workforces, and the need for 24/7 system availability have made remote access to privileged functions a necessity for many organizations.
The benefits are clear:
- Increased Efficiency and Productivity: Administrators can resolve issues and perform maintenance tasks remotely, eliminating the need for physical travel and reducing downtime.
- Improved Collaboration: Multiple administrators can collaborate on complex tasks, regardless of their physical location.
- Enhanced Disaster Recovery: Remote access enables administrators to quickly restore systems and data in the event of a disaster.
- 24/7 System Availability: Critical systems can be monitored and maintained around the clock, minimizing disruption to business operations.
However, these benefits come at a price. The expanded accessibility significantly increases the risk of unauthorized access, data breaches, and malicious attacks.
The Risks Associated with Remote Access to Privileged Functions
Permitting remote access to privileged functions introduces a multitude of security risks, including:
1. Credential Theft and Compromise:
This is arguably the most significant risk. Attackers employ various techniques, such as phishing, keyloggers, and man-in-the-middle attacks, to steal or compromise the credentials of privileged users. Once obtained, these credentials can grant attackers complete control over the system, potentially leading to data breaches, system sabotage, and financial losses.
2. Malware Infections:
Remote access tools can become entry points for malware. If an attacker compromises a remote access session, they can install malware on the target system, potentially granting them persistent access and escalating their privileges.
3. Insider Threats:
Even legitimate users with privileged access can pose a threat. Malicious insiders can misuse their privileges for personal gain or sabotage the organization. Negligent employees can also inadvertently expose systems to vulnerabilities.
4. Lateral Movement:
Once an attacker gains access to a system with privileged functions, they can use that access to move laterally within the network, gaining control over other systems and sensitive data.
5. Denial of Service (DoS) Attacks:
Attackers can launch DoS attacks against systems accessible through remote access, disrupting services and causing significant business disruption.
Mitigating the Risks: Strategies and Best Practices
The key to securing remote access to privileged functions is a multi-layered approach that combines robust security technologies with strong security policies and procedures.
1. Secure Remote Access Solutions:
Implement strong authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities. Avoid using easily guessable passwords or weak passwords. Use strong password managers and enforce regular password changes. Employ VPNs or jump servers to encrypt traffic and secure connections. Leverage technologies like Just-in-Time (JIT) access provisioning to grant temporary access only when needed, minimizing the window of vulnerability.
2. Least Privilege Principle:
Implement the principle of least privilege, granting users only the necessary privileges to perform their job functions. This limits the potential damage caused by compromised credentials or malicious insiders. Avoid giving users unnecessary elevated privileges. Use role-based access control (RBAC) to manage and control access permissions.
3. Regular Security Audits and Vulnerability Assessments:
Conduct regular security audits and vulnerability assessments to identify and address security weaknesses in your systems and remote access infrastructure. Patch systems promptly to address known vulnerabilities. Ensure that all software is up-to-date and well maintained.
4. Intrusion Detection and Prevention Systems (IDS/IPS):
Deploy IDS/IPS to monitor network traffic for suspicious activity, detect intrusions, and prevent malicious attacks. Implement network segmentation and traffic filtering to limit the impact of potential breaches.
5. Security Information and Event Management (SIEM):
Use SIEM systems to collect and analyze security logs from various sources, providing valuable insights into security incidents and helping to identify potential threats. Log all access attempts, successful or failed. Correlate events from multiple sources to detect patterns and anomalous behavior.
6. Strong Security Policies and Procedures:
Develop and enforce strong security policies and procedures that govern remote access to privileged functions. These policies should cover authentication, authorization, access control, data security, incident response, and employee training. Regular employee security training is essential to highlight these security policies and procedures.
7. Monitoring and Alerting:
Implement robust monitoring and alerting systems to detect suspicious activity in real-time. This allows for prompt responses to potential threats and minimizes the impact of security incidents.
8. Session Recording and Auditing:
Record and audit all remote access sessions to provide an audit trail of activity. This is invaluable for investigating security incidents and ensuring accountability. Implement robust logging mechanisms for all actions undertaken by privileged users.
Advanced Techniques for Enhanced Security
Beyond the basic mitigation strategies, several advanced techniques can further strengthen the security of remote access to privileged functions:
1. Privileged Access Management (PAM):
PAM solutions provide centralized management and control of privileged accounts, ensuring secure access and auditing of privileged activities. PAM solutions often integrate with other security tools, providing a comprehensive approach to privileged access management.
2. Deception Technology:
Deception technology uses decoys and traps to lure attackers and expose their tactics. This provides valuable intelligence on attacker behavior and helps to improve overall security posture.
3. Zero Trust Security:
Adopt a zero-trust security model, which assumes no implicit trust and verifies every access request, regardless of its origin. This minimizes the impact of compromised credentials or insider threats.
4. Endpoint Detection and Response (EDR):
EDR solutions monitor endpoint devices for malicious activity, providing real-time threat detection and response capabilities. This is crucial for detecting and responding to threats that may bypass other security controls.
Conclusion: Balancing Security and Functionality
Remote access to privileged functions is a critical component of modern IT infrastructure. However, it presents significant security risks that must be addressed with a robust and multi-layered security approach. By implementing the strategies and best practices outlined in this article, organizations can effectively mitigate these risks, ensuring both secure and efficient access to privileged functions. The key is to strike a balance between the benefits of remote access and the imperative to protect sensitive systems and data. A proactive and well-planned approach is crucial to achieving this balance and safeguarding the organization’s critical assets. Regular review and updates to security policies and procedures are vital to maintaining a strong security posture in the constantly evolving threat landscape. Investing in robust security technologies and training employees on secure practices is an essential investment in protecting the organization's valuable data and reputation.
Latest Posts
Latest Posts
-
A School Nutritionist Was Interested In How Students
Mar 17, 2025
-
A Customer Wants To Increase His Storage Capacity By 25gb
Mar 17, 2025
-
Tartaric Acid Has A Specific Rotation Of 12 0
Mar 17, 2025
-
Secretin Stimulates The To Secrete
Mar 17, 2025
-
What Is The Identity Of Element X From Part B
Mar 17, 2025
Related Post
Thank you for visiting our website which covers about Remote Access May Be Permitted For Privileged Functions . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
