Access To Sensitive Or Restricted Information Is Controlled
Holbox
Mar 24, 2025 · 6 min read
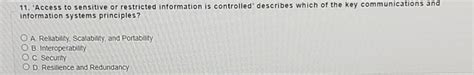
Table of Contents
- Access To Sensitive Or Restricted Information Is Controlled
- Table of Contents
- Access to Sensitive or Restricted Information is Controlled: A Deep Dive into Data Security
- The Importance of Controlled Access
- Financial Loss: Data breaches can result in significant financial losses due to theft, regulatory fines, legal fees, and damage to reputation. Think of the costs associated with credit card fraud, intellectual property theft, or ransomware attacks.
- Reputational Damage: A single data breach can severely damage an organization's reputation, leading to loss of customer trust and potential business failure. The impact on brand loyalty can be long-lasting.
- Legal and Regulatory Penalties: Many industries are subject to strict data protection regulations (like GDPR, CCPA, HIPAA). Failure to comply with these regulations can result in hefty fines and legal repercussions.
- National Security Risks: In the case of government or military data, unauthorized access poses a significant threat to national security, potentially compromising critical infrastructure or intelligence operations.
- Methods for Controlling Access to Sensitive Information
- Access Control Lists (ACLs): ACLs are fundamental to access control. They define which users or groups have permission to access specific files, folders, or resources. Permissions can be granular, allowing for fine-tuned control over read, write, execute, and other actions.
- Role-Based Access Control (RBAC): RBAC is a more advanced approach that assigns permissions based on roles within an organization. This simplifies management by grouping users with similar responsibilities and assigning permissions to those roles. For instance, an "administrator" role might have full access, while a "viewer" role only has read-only access.
- Attribute-Based Access Control (ABAC): ABAC is the most sophisticated approach, using attributes of users, resources, and the environment to determine access. This allows for extremely granular control based on various factors, such as location, time of day, or device type. For example, access to a sensitive document might be granted only to employees within a specific department, during business hours, and from company-owned devices.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access. This could involve a password, a security token, biometric authentication (fingerprint or facial recognition), or a one-time code sent to a mobile device.
- Data Encryption: Encryption transforms data into an unreadable format, protecting it even if it falls into the wrong hands. Encryption can be applied at various levels: at rest (when data is stored), in transit (when data is being transmitted), or in use (when data is being processed).
- Network Security: Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) are crucial for protecting networks from unauthorized access. These systems monitor network traffic, identify potential threats, and block malicious activity.
- Data Loss Prevention (DLP): DLP tools monitor data movement to prevent sensitive information from leaving the organization's control. These tools can scan emails, files, and other data streams for sensitive information and block or alert on unauthorized attempts to transfer it.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing help identify vulnerabilities in the security infrastructure. Penetration testing simulates real-world attacks to uncover weaknesses that could be exploited by malicious actors.
- Technologies Supporting Controlled Access
- Cloud Access Security Brokers (CASBs): CASBs provide a layer of security between users and cloud services, ensuring that access to cloud-based data is controlled and secure. They can enforce security policies, monitor user activity, and prevent data breaches.
- Identity and Access Management (IAM) Systems: IAM systems manage user identities and access rights across multiple systems and applications. They centralize user management, simplify access control, and improve overall security.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security logs from various sources to identify and respond to security threats. They provide real-time monitoring, threat detection, and incident response capabilities.
- Endpoint Detection and Response (EDR) Solutions: EDR solutions monitor endpoint devices (laptops, desktops, mobile devices) for malicious activity. They provide visibility into endpoint behavior, enabling rapid detection and response to threats.
- Best Practices for Controlling Access
- Principle of Least Privilege: Users should only be granted the minimum level of access necessary to perform their job functions. This limits the potential damage caused by a compromised account.
- Regular Password Changes: Enforce strong passwords and require regular password changes to prevent unauthorized access. Consider implementing password managers to help users create and manage strong passwords securely.
- Employee Training and Awareness: Educate employees about security risks and best practices, such as phishing scams, social engineering attacks, and the importance of strong passwords.
- Data Classification and Labeling: Classify data based on its sensitivity and label it accordingly. This helps determine appropriate access control measures for different types of information.
- Regular Security Assessments: Conduct regular security assessments to identify and address vulnerabilities. This includes vulnerability scanning, penetration testing, and security audits.
- Incident Response Plan: Develop and test an incident response plan to handle data breaches and other security incidents effectively. This plan should outline procedures for containment, eradication, recovery, and post-incident activity.
- Data Backup and Recovery: Implement a robust data backup and recovery strategy to ensure data availability in the event of a data loss incident. Regular backups should be stored securely, ideally in a geographically separate location.
- The Future of Controlled Access
- Conclusion
- Latest Posts
- Latest Posts
- Related Post
Access to Sensitive or Restricted Information is Controlled: A Deep Dive into Data Security
The digital age has ushered in an era of unprecedented data creation and storage. This abundance of information, however, comes with significant security challenges. Protecting sensitive or restricted information is paramount, not only for individual privacy but also for the integrity of organizations and national security. This article delves into the multifaceted world of controlled access to sensitive information, exploring various methods, technologies, and best practices.
The Importance of Controlled Access
Controlled access to sensitive information isn't just a good idea; it's a necessity. The consequences of unauthorized access can be devastating, leading to:
Financial Loss: Data breaches can result in significant financial losses due to theft, regulatory fines, legal fees, and damage to reputation. Think of the costs associated with credit card fraud, intellectual property theft, or ransomware attacks.
Reputational Damage: A single data breach can severely damage an organization's reputation, leading to loss of customer trust and potential business failure. The impact on brand loyalty can be long-lasting.
Legal and Regulatory Penalties: Many industries are subject to strict data protection regulations (like GDPR, CCPA, HIPAA). Failure to comply with these regulations can result in hefty fines and legal repercussions.
National Security Risks: In the case of government or military data, unauthorized access poses a significant threat to national security, potentially compromising critical infrastructure or intelligence operations.
Methods for Controlling Access to Sensitive Information
Numerous methods are employed to control access to sensitive or restricted information. These methods often work in concert to create a robust security posture:
Access Control Lists (ACLs): ACLs are fundamental to access control. They define which users or groups have permission to access specific files, folders, or resources. Permissions can be granular, allowing for fine-tuned control over read, write, execute, and other actions.
Role-Based Access Control (RBAC): RBAC is a more advanced approach that assigns permissions based on roles within an organization. This simplifies management by grouping users with similar responsibilities and assigning permissions to those roles. For instance, an "administrator" role might have full access, while a "viewer" role only has read-only access.
Attribute-Based Access Control (ABAC): ABAC is the most sophisticated approach, using attributes of users, resources, and the environment to determine access. This allows for extremely granular control based on various factors, such as location, time of day, or device type. For example, access to a sensitive document might be granted only to employees within a specific department, during business hours, and from company-owned devices.
Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access. This could involve a password, a security token, biometric authentication (fingerprint or facial recognition), or a one-time code sent to a mobile device.
Data Encryption: Encryption transforms data into an unreadable format, protecting it even if it falls into the wrong hands. Encryption can be applied at various levels: at rest (when data is stored), in transit (when data is being transmitted), or in use (when data is being processed).
Network Security: Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) are crucial for protecting networks from unauthorized access. These systems monitor network traffic, identify potential threats, and block malicious activity.
Data Loss Prevention (DLP): DLP tools monitor data movement to prevent sensitive information from leaving the organization's control. These tools can scan emails, files, and other data streams for sensitive information and block or alert on unauthorized attempts to transfer it.
Regular Security Audits and Penetration Testing: Regular security audits and penetration testing help identify vulnerabilities in the security infrastructure. Penetration testing simulates real-world attacks to uncover weaknesses that could be exploited by malicious actors.
Technologies Supporting Controlled Access
Several technologies play a pivotal role in implementing and managing controlled access:
Cloud Access Security Brokers (CASBs): CASBs provide a layer of security between users and cloud services, ensuring that access to cloud-based data is controlled and secure. They can enforce security policies, monitor user activity, and prevent data breaches.
Identity and Access Management (IAM) Systems: IAM systems manage user identities and access rights across multiple systems and applications. They centralize user management, simplify access control, and improve overall security.
Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security logs from various sources to identify and respond to security threats. They provide real-time monitoring, threat detection, and incident response capabilities.
Endpoint Detection and Response (EDR) Solutions: EDR solutions monitor endpoint devices (laptops, desktops, mobile devices) for malicious activity. They provide visibility into endpoint behavior, enabling rapid detection and response to threats.
Best Practices for Controlling Access
Implementing robust access control requires a multifaceted approach that incorporates best practices:
Principle of Least Privilege: Users should only be granted the minimum level of access necessary to perform their job functions. This limits the potential damage caused by a compromised account.
Regular Password Changes: Enforce strong passwords and require regular password changes to prevent unauthorized access. Consider implementing password managers to help users create and manage strong passwords securely.
Employee Training and Awareness: Educate employees about security risks and best practices, such as phishing scams, social engineering attacks, and the importance of strong passwords.
Data Classification and Labeling: Classify data based on its sensitivity and label it accordingly. This helps determine appropriate access control measures for different types of information.
Regular Security Assessments: Conduct regular security assessments to identify and address vulnerabilities. This includes vulnerability scanning, penetration testing, and security audits.
Incident Response Plan: Develop and test an incident response plan to handle data breaches and other security incidents effectively. This plan should outline procedures for containment, eradication, recovery, and post-incident activity.
Data Backup and Recovery: Implement a robust data backup and recovery strategy to ensure data availability in the event of a data loss incident. Regular backups should be stored securely, ideally in a geographically separate location.
The Future of Controlled Access
The landscape of data security is constantly evolving, with new technologies and threats emerging regularly. The future of controlled access will likely involve:
-
Increased reliance on AI and machine learning: AI and machine learning will play an increasingly important role in automating security tasks, detecting threats, and improving access control.
-
Zero Trust Security: Zero trust models assume no implicit trust and verify every access request, regardless of location or device.
-
Blockchain technology: Blockchain can provide a secure and transparent way to manage access control and track data access history.
-
Quantum-resistant cryptography: As quantum computing advances, the need for quantum-resistant cryptographic algorithms will become increasingly important.
Conclusion
Controlling access to sensitive or restricted information is crucial for protecting individual privacy, organizational integrity, and national security. A robust access control strategy requires a multi-layered approach encompassing various methods, technologies, and best practices. By implementing these measures and staying abreast of the latest security trends, organizations and individuals can significantly reduce the risk of data breaches and protect their valuable information. The continuous evolution of technology necessitates a proactive and adaptable security posture to effectively manage the ever-growing challenges in data protection. Proactive security measures, regular updates, and consistent training are key to maintaining a strong defense against ever-evolving threats to sensitive information.
Latest Posts
Latest Posts
-
Gathering The Information Needed And Then Setting Departmental Goals
Mar 26, 2025
-
Write The Balanced Chemical Equation For The Reaction Shown
Mar 26, 2025
-
Rewrite This Measurement With A Simpler Unit If Possible
Mar 26, 2025
-
The Bedford Guide For College Writers
Mar 26, 2025
-
When Caring For Terminally Ill Patients You Should
Mar 26, 2025
Related Post
Thank you for visiting our website which covers about Access To Sensitive Or Restricted Information Is Controlled . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
