Which Of The Following Are Included In The Opsec Cycle
Holbox
Mar 17, 2025 · 6 min read
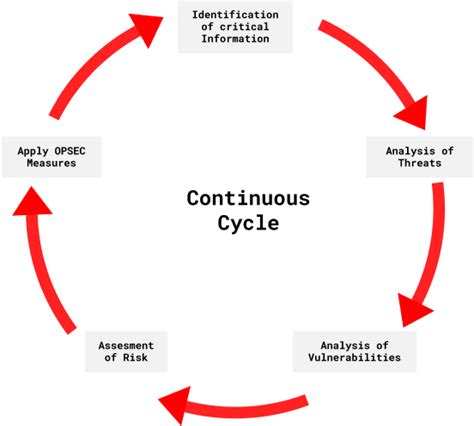
Table of Contents
Which of the Following are Included in the OPSEC Cycle? A Comprehensive Guide
Operational Security (OPSEC) is a critical process for protecting sensitive information and maintaining a competitive edge, particularly in high-stakes environments like business, government, and the military. Understanding the OPSEC cycle is crucial for implementing effective security measures. This comprehensive guide delves into the key components of the OPSEC cycle, providing a detailed explanation of each stage and offering practical examples to enhance your understanding.
The Five Steps of the OPSEC Cycle
The OPSEC cycle is a five-step process designed to systematically identify, analyze, and mitigate vulnerabilities that could compromise sensitive information. These five steps are iterative and should be revisited regularly to ensure ongoing effectiveness. Failing to address any one stage weakens the entire process.
1. Identify Critical Information: The Foundation of OPSEC
This is the foundational step. It requires a thorough and meticulous assessment of all information that, if compromised, could significantly harm your organization's interests. This isn't just about obvious secrets; it's about identifying anything that could provide an adversary with a valuable advantage.
What to Consider:
- Business Strategies: Long-term plans, market analysis, product development roadmaps, and financial forecasts.
- Technology: Proprietary algorithms, software code, network architecture, and hardware specifications.
- Personnel: Employee identities, contact information, travel schedules, and security clearances.
- Operations: Daily routines, logistical information, supply chains, and communication protocols.
- Intellectual Property: Patents, trademarks, designs, and trade secrets.
Techniques for Identification:
- Brainstorming Sessions: Engage various team members from different departments to gain diverse perspectives.
- Threat Modeling: Analyze potential threats and their likely methods of attack to pinpoint vulnerabilities.
- Vulnerability Assessments: Conduct regular assessments of your systems and infrastructure to identify weaknesses.
- Reviewing Past Incidents: Analyze previous security breaches to identify patterns and recurring vulnerabilities.
Example: A pharmaceutical company would consider its research and development data on new drugs as critical information, as its leak would allow competitors to quickly replicate their work. Similarly, a tech startup would need to protect its source code and algorithms.
2. Analyze Threats: Understanding the Enemy
Once critical information is identified, you must analyze the potential threats that could target it. This involves identifying who might want to access this information, their capabilities, and their likely methods of obtaining it.
Who are your threats?
- Competitors: Businesses vying for market share might seek to steal trade secrets or intellectual property.
- Hackers: Individuals or groups motivated by financial gain, political agendas, or simply the thrill of the challenge.
- Foreign Governments: State-sponsored actors seeking to obtain economic or military intelligence.
- Insider Threats: Disgruntled employees or contractors who might leak information intentionally or unintentionally.
What are their capabilities?
- Technical Skills: Do they possess the necessary technical expertise to exploit vulnerabilities?
- Resources: Do they have the financial resources and time to launch an attack?
- Motivation: What are their motives, and how strongly are they driven to obtain the information?
Example: A defense contractor needs to consider state-sponsored hacking groups as potential threats to their classified military technologies. A small business might focus on competitors' attempts at industrial espionage.
3. Analyze Vulnerabilities: Identifying Weak Points
This step involves identifying weaknesses in your security posture that could be exploited by adversaries to access your critical information. This analysis must be comprehensive, examining all aspects of your operations.
Common Vulnerabilities:
- Unpatched Software: Outdated software with known security flaws creates easily exploitable entry points.
- Weak Passwords: Easily guessed or cracked passwords provide easy access to systems and data.
- Poor Physical Security: Inadequate security measures for physical access to facilities and equipment.
- Insider Threats: Unvetted or disaffected employees present a significant risk.
- Social Engineering: Manipulating individuals to divulge sensitive information.
- Unsecured Wireless Networks: Open Wi-Fi networks expose sensitive data to interception.
Techniques for Vulnerability Analysis:
- Penetration Testing: Simulating real-world attacks to identify weaknesses in security systems.
- Security Audits: Regular reviews of security policies, procedures, and controls.
- Risk Assessments: Evaluating the likelihood and impact of potential security breaches.
Example: A company using outdated email software with known vulnerabilities is leaving itself open to phishing attacks that could compromise employee credentials.
4. Develop Countermeasures: Mitigating Risks
Based on your analysis of threats and vulnerabilities, you need to develop countermeasures to protect your critical information. These should be tailored to the specific risks identified and should address both technical and human factors.
Types of Countermeasures:
- Technical Controls: Encryption, firewalls, intrusion detection systems, and access control lists.
- Physical Controls: Security guards, surveillance cameras, secure access control systems, and physical barriers.
- Administrative Controls: Security awareness training, incident response plans, and background checks for employees.
Example: To counter the threat of phishing attacks, a company might implement email filtering software, conduct security awareness training for employees, and establish clear policies for handling suspicious emails.
5. Implement and Review: Continuous Improvement
The final step involves implementing the chosen countermeasures and regularly reviewing their effectiveness. This is not a one-time process; it requires ongoing monitoring, adaptation, and improvement.
Implementation:
- Training: Ensure all employees understand their roles and responsibilities in maintaining OPSEC.
- Testing: Regularly test the effectiveness of your countermeasures to identify weaknesses.
- Documentation: Maintain clear documentation of all OPSEC procedures and policies.
Review and Improvement:
- Regular Assessments: Periodically assess your OPSEC program to identify areas for improvement.
- Feedback Mechanisms: Establish channels for employees to report security concerns.
- Adaptation: Continuously adapt your OPSEC strategies to address evolving threats and vulnerabilities.
Example: The company implementing email filtering software should regularly review the effectiveness of the filter, adjusting its settings as needed to counter new phishing techniques. They should also regularly train employees on the latest phishing tactics.
The Importance of Continuous Improvement in the OPSEC Cycle
The OPSEC cycle is not a static process. It requires continuous monitoring, adaptation, and improvement to remain effective. Threats and vulnerabilities are constantly evolving, requiring a dynamic approach to security. Regular review of each step – from identifying critical information to implementing and reviewing countermeasures – is crucial for ensuring the long-term success of your OPSEC program. Failing to adapt to new threats can leave your organization exposed to significant risks.
Integrating OPSEC into Your Organization's Culture
Successful OPSEC implementation requires more than just technical measures; it requires a cultural shift within the organization. Employees at all levels must understand the importance of protecting sensitive information and actively participate in maintaining security. This necessitates:
- Comprehensive Training: Regular training programs covering various aspects of OPSEC, including social engineering awareness, password security, and physical security protocols.
- Clear Communication: Establishing clear communication channels for reporting security incidents and raising concerns.
- Incentivization: Recognizing and rewarding employees for their contributions to OPSEC.
- Accountability: Implementing clear accountability mechanisms for security breaches and violations.
By integrating OPSEC into the organizational culture, you cultivate a proactive security mindset, significantly enhancing the effectiveness of your overall security program.
Conclusion: OPSEC – An Ongoing Commitment
Operational Security is not a one-time project but a continuous process demanding vigilance and adaptation. By diligently following the five steps of the OPSEC cycle and integrating OPSEC into your organizational culture, you can significantly reduce your vulnerability to threats and protect your critical information. Remember that even small oversights can have significant consequences, so consistent effort and a proactive approach are paramount. Regular reviews and updates are essential to staying ahead of evolving threats and ensuring the long-term success of your OPSEC program. This ensures the protection of your valuable assets and helps maintain a competitive edge in today's dynamic and challenging environment.
Latest Posts
Latest Posts
-
The Alcoholic Beverages In A Private Club Are
Mar 18, 2025
-
Garbage Container Used By An Operation Should Be
Mar 18, 2025
-
The Macroenvironment Is Also Known As The Blank Environment
Mar 18, 2025
-
Imagery And Repetition Are Aspects Of
Mar 18, 2025
-
Can You Highlight In Rented Chegg Books
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Are Included In The Opsec Cycle . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
