What Is The Purpose Of The Checksum Tcp Field
Holbox
Mar 28, 2025 · 6 min read
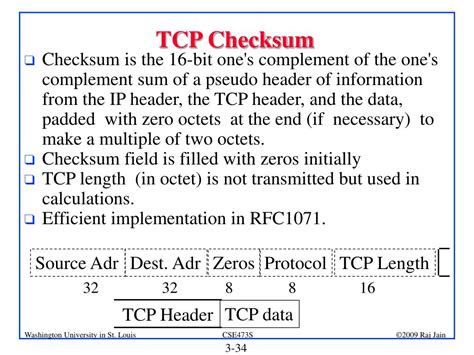
Table of Contents
- What Is The Purpose Of The Checksum Tcp Field
- Table of Contents
- What is the Purpose of the Checksum TCP Field? Ensuring Data Integrity in Network Transmission
- The Role of Error Detection in Data Transmission
- Understanding the TCP Checksum: A Deep Dive
- How the Checksum is Calculated
- The Importance of the Pseudo-header
- Beyond Error Detection: Implications for Security
- Limitations of the TCP Checksum
- Enhancements and Alternatives
- Conclusion: The Vital Role of the TCP Checksum
- Latest Posts
- Latest Posts
- Related Post
What is the Purpose of the Checksum TCP Field? Ensuring Data Integrity in Network Transmission
The internet, a vast network connecting billions of devices, relies on robust protocols to ensure reliable data transmission. At the heart of this reliability lies the Transmission Control Protocol (TCP), a cornerstone of the internet's architecture. Within the TCP header resides a crucial field: the checksum. Understanding its purpose is fundamental to grasping how TCP maintains data integrity across potentially unreliable networks. This comprehensive guide will delve into the intricacies of the TCP checksum, explaining its functionality, importance, and implications for network security.
The Role of Error Detection in Data Transmission
Before diving into the specifics of the TCP checksum, it's crucial to understand the broader context of error detection in network communication. Data transmitted across networks is susceptible to corruption due to various factors, including:
- Noise: Electrical interference and other environmental factors can alter bits during transmission.
- Hardware Failures: Faulty network interfaces or transmission lines can introduce errors.
- Software Bugs: Errors in network drivers or protocol implementations can lead to corrupted data.
Without mechanisms for error detection, corrupted data could lead to application malfunctions, data loss, and system instability. Checksums, including the TCP checksum, provide a critical layer of defense against these potential problems.
Understanding the TCP Checksum: A Deep Dive
The TCP checksum is a 16-bit field located within the TCP header. Its primary purpose is to detect errors that may have occurred during the transmission of the TCP segment. It's a crucial component of TCP's reliability features, ensuring that the data received is identical to the data sent.
How the Checksum is Calculated
The checksum calculation isn't a simple sum of the TCP header and data. Instead, it involves a more sophisticated process:
-
Pseudo-header Inclusion: The checksum calculation incorporates a pseudo-header that includes information not directly part of the TCP header, such as the source and destination IP addresses, protocol number (TCP in this case), and TCP segment length. This inclusion enhances the robustness of the checksum by considering network-layer information.
-
One's Complement Summation: The TCP header and data are treated as a sequence of 16-bit words. These words are added together using one's complement arithmetic. This arithmetic simplifies the detection of errors, especially single-bit errors.
-
One's Complement: The final sum from step 2 is then complemented (all bits are flipped: 0s become 1s, and 1s become 0s). This complemented sum forms the TCP checksum.
-
Verification at the Receiver: The receiver performs the same checksum calculation on the received TCP segment, including the pseudo-header. If the resulting checksum matches the received checksum, the data is considered error-free. A mismatch indicates an error in transmission.
The Importance of the Pseudo-header
The inclusion of the pseudo-header is a vital element of the TCP checksum's effectiveness. By including IP-layer information, the checksum covers potential errors introduced not just within the TCP segment itself but also at the network layer. This ensures that errors introduced during routing or network-level transmission are also detected.
Beyond Error Detection: Implications for Security
While primarily designed for error detection, the TCP checksum also plays an indirect role in network security. Although it doesn't directly prevent attacks, it can contribute to their detection:
-
Tampering Detection: If an attacker attempts to modify the TCP segment's data or header, the checksum calculation at the receiver will detect the alteration, indicating a potential security breach. This allows for the rejection of tampered packets.
-
Integrity Verification: The checksum acts as a simple form of data integrity check. It verifies that the received data is consistent with the transmitted data, helping prevent subtle attacks that might alter data without causing obvious transmission errors.
However, it's crucial to understand that the TCP checksum is not a foolproof security mechanism. Sophisticated attacks can circumvent it, particularly those that carefully manipulate the checksum to match the modified data. Therefore, the TCP checksum should be seen as a supplementary security measure, not a primary defense against attacks. More robust security protocols and mechanisms are necessary for strong network security.
Limitations of the TCP Checksum
While effective in many situations, the TCP checksum has limitations:
-
Limited Error Detection: The checksum is not capable of detecting all types of errors. It may miss certain types of complex errors, such as those involving multiple bit flips that cancel each other out during the checksum calculation.
-
Not a Cryptographic Hash: The TCP checksum is not a cryptographic hash function. It lacks the properties necessary to provide strong cryptographic security guarantees. It cannot provide authentication or prevent sophisticated attacks that involve careful manipulation of the checksum.
-
Vulnerability to Certain Attacks: As previously mentioned, the checksum is vulnerable to carefully crafted attacks that modify both the data and the checksum to create a valid but malicious packet.
Enhancements and Alternatives
Due to the limitations of the TCP checksum, several enhancements and alternatives have been explored:
-
CRC (Cyclic Redundancy Check): CRC is a more robust error detection mechanism that offers better error detection capabilities than the simple checksum used by TCP.
-
Cryptographic Hash Functions (e.g., SHA-256, MD5): These functions provide significantly stronger security and data integrity guarantees compared to the TCP checksum, offering resistance against tampering and unauthorized modifications. However, they are computationally more expensive.
-
IPsec (Internet Protocol Security): IPsec provides a comprehensive set of security services, including data integrity and authentication, using cryptographic techniques that are far superior to the simple checksum approach.
Conclusion: The Vital Role of the TCP Checksum
The TCP checksum, despite its limitations, remains a critical component of the TCP protocol. Its purpose is to provide a basic level of error detection, ensuring the reliability of data transmission across the internet. While it doesn't offer strong security guarantees, it plays an important role in detecting accidental errors and, to a lesser extent, some forms of malicious manipulation. Its simplicity and relatively low computational cost make it a practical solution for ensuring the reliable delivery of vast amounts of data across the network. Understanding its strengths and weaknesses is crucial for appreciating the complex interplay of error detection and security in modern network communication. While more sophisticated mechanisms are used for robust security and advanced error detection, the TCP checksum continues to play a foundational role in ensuring the internet's reliable operation. The ongoing development and evolution of network protocols highlight the persistent need for improved error detection and security measures, but the TCP checksum remains a significant component in the history and present of network communication.
Latest Posts
Latest Posts
-
Which Of The Following Best Describes A Misrepresentation
Mar 31, 2025
-
Another Common Term For Stockholders Equity Is
Mar 31, 2025
-
In Equity Theory Employees Are Motivated To
Mar 31, 2025
-
A Gallup Poll Conducted Telephone Interviews
Mar 31, 2025
-
Increasing Inventory Turnover Rate Will Improve Profitability
Mar 31, 2025
Related Post
Thank you for visiting our website which covers about What Is The Purpose Of The Checksum Tcp Field . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
