War Driving Is Not A Type Of Wireless Piggybacking
Holbox
Mar 30, 2025 · 6 min read
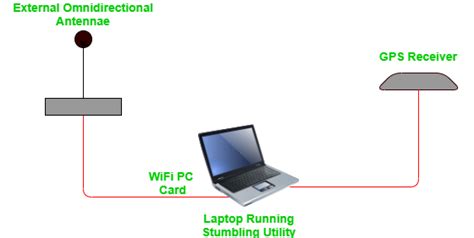
Table of Contents
- War Driving Is Not A Type Of Wireless Piggybacking
- Table of Contents
- War Driving is Not a Type of Wireless Piggybacking: Understanding the Key Differences
- Defining War Driving
- Defining Wireless Piggybacking
- Key Differences Between War Driving and Wireless Piggybacking: A Comparative Analysis
- Dispelling Common Misconceptions
- Protecting Your Wireless Network
- Conclusion: A Clear Distinction
- Latest Posts
- Latest Posts
- Related Post
War Driving is Not a Type of Wireless Piggybacking: Understanding the Key Differences
War driving and wireless piggybacking are often conflated, leading to significant misunderstandings about the nature of each activity and their legal implications. While both involve accessing wireless networks, their motivations, methods, and consequences differ substantially. This article will delve into the distinctions between war driving and wireless piggybacking, clarifying the crucial differences and dispelling common misconceptions.
Defining War Driving
War driving is the act of mobile reconnaissance of wireless networks. Individuals, often using specialized software and hardware, travel in vehicles or on foot, actively scanning for nearby Wi-Fi networks. The primary goal isn't necessarily to gain unauthorized access to these networks, although that might be a secondary objective. Instead, war driving aims to:
- Map Wireless Network Coverage: This is often done for research purposes, identifying areas with strong Wi-Fi signals, weak spots in coverage, or the density of networks in a particular location.
- Identify Security Vulnerabilities: War drivers might look for networks with weak passwords, open access points, or outdated security protocols. This information could be used to highlight security risks for network owners or for malicious purposes.
- Test Network Performance: By detecting signal strength and assessing network stability from various locations, war drivers can assess the overall performance of a wireless network infrastructure.
Methods employed in war driving often involve:
- Specialized Software: Software applications are used to detect and identify nearby Wi-Fi networks, displaying SSID (Service Set Identifier), signal strength, security protocols used (WPA2, WEP, etc.), and sometimes even the MAC address of the access point.
- Laptop or Mobile Device: A laptop or mobile device equipped with a wireless network adapter is essential for scanning and data collection.
- GPS Device or Mapping Software: Integrating a GPS device or using mapping software provides geolocation data, allowing war drivers to map the location of the detected wireless networks.
- Vehicle or Foot Travel: The act of physically moving through an area to map network coverage is a defining characteristic of war driving.
Ethical Considerations:
While war driving itself isn't inherently illegal, the intent and subsequent actions can have legal consequences. Mapping wireless networks for legitimate research or security testing usually falls into a grey area, while using the information obtained to gain unauthorized access is clearly illegal. Ethical considerations revolve around respecting network owners' privacy and refraining from activities that could lead to harm or disruption. Obtaining informed consent from network owners before scanning their networks is generally the most responsible approach.
Defining Wireless Piggybacking
Wireless piggybacking, also known as unauthorized access to a wireless network, involves directly connecting to a Wi-Fi network without the owner's permission. Unlike war driving, the primary goal is to gain access to the network's resources. This might involve:
- Accessing the Internet: The most common motive is to obtain free internet access without paying for a service.
- Stealing Data: Malicious actors might access the network to steal sensitive data, including personal information, financial details, or intellectual property.
- Launching Attacks: Piggybacking can be used as a stepping stone to launch further attacks on other devices within the network.
Methods used in wireless piggybacking often include:
- Cracking Passwords: This involves attempting to guess or brute-force the network's password.
- Exploiting Vulnerabilities: Attackers might exploit known vulnerabilities in the network's security protocols or access point firmware to gain unauthorized access.
- Using Pre-shared Keys: In some cases, individuals might gain access through obtaining the network's pre-shared key.
- Connecting to Open Networks: Connecting to a Wi-Fi network that is intentionally left open is technically still piggybacking, albeit a less malicious variant.
Legal Ramifications:
Wireless piggybacking is explicitly illegal in most jurisdictions. Unauthorized access to a computer system or network is a serious offense, often carrying significant fines and potential imprisonment. The severity of the penalties will depend on factors such as the intent of the attacker, the type of data accessed, and the resulting damage.
Key Differences Between War Driving and Wireless Piggybacking: A Comparative Analysis
| Feature | War Driving | Wireless Piggybacking |
|---|---|---|
| Primary Goal | Reconnaissance, Mapping, Vulnerability Assessment | Unauthorized Access to Network Resources |
| Motivation | Research, Security Testing, Network Analysis | Free Internet, Data Theft, Launching Attacks |
| Method | Passive Scanning, Data Collection | Active Connection, Password Cracking, Exploit Use |
| Legality | Mostly legal (dependent on intent and subsequent actions) | Illegal |
| Ethical Concerns | Respecting privacy, avoiding harm | Violating privacy, potential for significant harm |
| Impact | Potentially informative, could reveal vulnerabilities | Data breaches, disruption of services, financial loss |
Dispelling Common Misconceptions
Several misconceptions often blur the lines between war driving and wireless piggybacking:
- Misconception 1: All war driving is illegal: While some war driving activities might have legal implications if they violate privacy laws or lead to unauthorized access, the act of simply scanning for networks is not inherently illegal.
- Misconception 2: Piggybacking is a type of war driving: Piggybacking is a distinct activity. War driving is about reconnaissance; piggybacking is about unauthorized access and use.
- Misconception 3: Open networks are free for all: While open networks lack password protection, connecting to them without the owner's implicit or explicit permission still constitutes piggybacking. The owner could change their mind and impose restrictions.
- Misconception 4: War drivers are always malicious: Many war drivers conduct their activities with ethical considerations in mind, aiming to improve network security or gain a better understanding of network coverage.
Protecting Your Wireless Network
Understanding the differences between war driving and wireless piggybacking allows you to take appropriate measures to secure your network:
- Strong Passwords: Use a strong and unique password that is difficult to guess or crack.
- Updated Security Protocols: Ensure your router uses the latest and most secure encryption protocol, such as WPA3.
- Regular Firmware Updates: Keep your router's firmware up-to-date to patch known vulnerabilities.
- MAC Address Filtering: Restrict access to your network based on the MAC addresses of authorized devices. Note that this is not an impenetrable security measure.
- Firewall: Implement a firewall to further protect your network from unauthorized access.
- Network Monitoring: Regularly monitor your network activity for suspicious connections.
Conclusion: A Clear Distinction
War driving and wireless piggybacking are two distinct activities with vastly different implications. While war driving, in its purest form, focuses on mapping and identifying networks, wireless piggybacking constitutes illegal and potentially harmful unauthorized access. Understanding these differences is crucial for responsible network usage, ethical considerations, and avoiding legal repercussions. By taking appropriate security measures and understanding the potential risks, network owners can effectively protect their systems and data from malicious actors. Remember, responsible digital citizenship dictates respecting the boundaries of others’ networks and adhering to the laws governing network access.
Latest Posts
Latest Posts
-
High And Persistent Inflation Is Caused By
Apr 02, 2025
-
Classify Whether Each Compound Contains An Ionic Bond
Apr 02, 2025
-
Obvious Elder Abuse Is More Likely To Occur
Apr 02, 2025
-
An Elderly Widower You Care For
Apr 02, 2025
-
Medical Language For Modern Health Care
Apr 02, 2025
Related Post
Thank you for visiting our website which covers about War Driving Is Not A Type Of Wireless Piggybacking . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
