Opsec Is A Cycle Used To Identify Analyze And Control
Holbox
Apr 01, 2025 · 6 min read
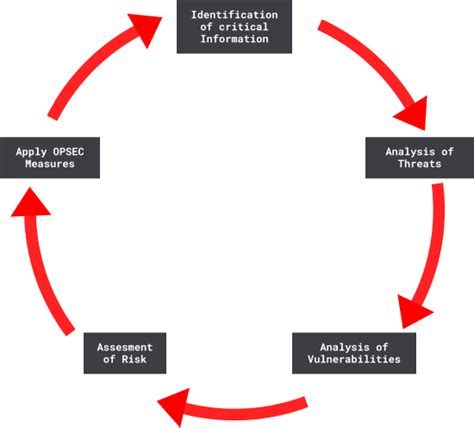
Table of Contents
- Opsec Is A Cycle Used To Identify Analyze And Control
- Table of Contents
- OPSEC: A Continuous Cycle of Identification, Analysis, and Control
- Understanding the OPSEC Cycle: It's Not Linear
- Stage 1: Identifying Critical Information (CI) – The Foundation of OPSEC
- Types of Critical Information:
- Techniques for Identifying CI:
- Stage 2: Analyzing Threats and Vulnerabilities – Understanding the Risks
- Identifying Potential Threats:
- Vulnerability Assessment Techniques:
- Stage 3: Developing and Implementing Control Measures – Mitigation Strategies
- Types of Control Measures:
- Implementing Control Measures Effectively:
- Stage 4: Continuous Monitoring and Assessment – The Cycle Continues
- Continuous Monitoring Activities:
- Adapting to the Evolving Threat Landscape:
- The Importance of Human Factors in OPSEC
- Conclusion: OPSEC – A Never-Ending Journey
- Latest Posts
- Latest Posts
- Related Post
OPSEC: A Continuous Cycle of Identification, Analysis, and Control
Operational Security (OPSEC) isn't a one-time fix; it's a dynamic, continuous cycle. Think of it less as a checklist and more as a living, breathing process that requires constant vigilance and adaptation. This article delves into the cyclical nature of OPSEC, exploring the key stages of identification, analysis, and control, and emphasizes the importance of continuous improvement and proactive measures.
Understanding the OPSEC Cycle: It's Not Linear
Many mistakenly perceive OPSEC as a linear process, completed once a specific checklist is ticked off. This is a dangerous misconception. The true power of OPSEC lies in its cyclical nature. The process is iterative, constantly evolving to meet emerging threats and vulnerabilities. It's a continuous loop of identifying critical information, analyzing potential threats, implementing control measures, and then reassessing and refining the entire process. This iterative approach ensures that your OPSEC strategy remains relevant and effective in the face of ever-changing circumstances.
Stage 1: Identifying Critical Information (CI) – The Foundation of OPSEC
This initial stage is crucial. It forms the very foundation upon which your entire OPSEC strategy rests. Critical Information (CI) is any information that, if compromised, could significantly damage your operations, reputation, or security. This isn't just about classified documents; CI can encompass a broad spectrum of data:
Types of Critical Information:
- Operational Plans and Procedures: Details about your organization's internal workings, including strategies, tactics, and procedures.
- Personnel Information: Sensitive data about employees, contractors, or clients, such as personal details, contact information, and employment history.
- Financial Data: Account numbers, financial statements, budgets, and any other information that could lead to financial loss or fraud.
- Technological Information: Details about your organization's IT infrastructure, software systems, and security protocols.
- Physical Security Information: Information about your organization's physical security measures, including building layouts, access controls, and security personnel.
- Intellectual Property: Patents, trademarks, copyrights, and any other proprietary information that gives your organization a competitive advantage.
- Communication Methods: Details about your organization's communication channels, including email addresses, phone numbers, and messaging platforms.
Techniques for Identifying CI:
- Brainstorming Sessions: Gather key personnel from various departments to collaboratively identify potential vulnerabilities.
- Threat Modeling: Systematically analyze your operations and identify potential threats and vulnerabilities.
- Vulnerability Assessments: Conduct regular assessments to identify weaknesses in your security posture.
- Red Teaming/Penetration Testing: Simulate attacks to identify vulnerabilities and weaknesses in your defenses.
- Review of Past Incidents: Analyze past security breaches to identify recurring patterns and vulnerabilities.
Stage 2: Analyzing Threats and Vulnerabilities – Understanding the Risks
Once you've identified your CI, the next step is to analyze the potential threats and vulnerabilities that could lead to its compromise. This involves considering various factors:
Identifying Potential Threats:
- Adversaries: Identify potential adversaries who might be interested in obtaining your CI. This could include competitors, hackers, foreign governments, or disgruntled employees.
- Threat Actors' Capabilities: Analyze the capabilities and resources of these adversaries. Understand their technical skills, resources, and motivation.
- Methods of Attack: Consider the various methods that adversaries might use to obtain your CI. This could include phishing, malware, social engineering, physical intrusion, or insider threats.
- Vulnerabilities: Identify vulnerabilities in your security posture that could be exploited by adversaries. This could include weaknesses in your IT infrastructure, physical security, or personnel security.
Vulnerability Assessment Techniques:
- Network Scanning: Identify open ports and vulnerabilities in your network infrastructure.
- Software Vulnerability Scanning: Identify vulnerabilities in your software applications and operating systems.
- Social Engineering Simulations: Test your employees' ability to resist social engineering attacks.
- Penetration Testing: Simulate real-world attacks to identify vulnerabilities in your security posture.
- Risk Assessments: Evaluate the likelihood and impact of different threats and vulnerabilities.
Stage 3: Developing and Implementing Control Measures – Mitigation Strategies
This is where you actively work to mitigate the identified threats and vulnerabilities. Control measures should be tailored to address specific risks and vulnerabilities. Effective control measures are multifaceted and integrated:
Types of Control Measures:
- Physical Security Controls: Access control systems, surveillance cameras, security personnel, and perimeter security.
- Technical Security Controls: Firewalls, intrusion detection systems, antivirus software, data encryption, and multi-factor authentication.
- Administrative Security Controls: Security policies, procedures, training programs, and background checks.
- Personnel Security Controls: Background checks, security awareness training, and clear security protocols for employees.
- Procedural Security Controls: Establishing clear procedures for handling sensitive information, including data storage, access control, and disposal.
- Communication Security Controls: Secure communication channels, encryption, and protocols for handling sensitive information.
Implementing Control Measures Effectively:
- Prioritization: Focus on implementing controls that address the highest-risk vulnerabilities first.
- Integration: Integrate various control measures to create a layered security approach.
- Testing: Regularly test control measures to ensure their effectiveness.
- Documentation: Maintain thorough documentation of all security policies and procedures.
- Training: Provide regular security awareness training to all employees.
Stage 4: Continuous Monitoring and Assessment – The Cycle Continues
The OPSEC cycle doesn't end with the implementation of control measures. Continuous monitoring and assessment are vital to ensure the effectiveness of your strategy. This ongoing evaluation allows for timely adjustments and improvements based on emerging threats, changing circumstances, and lessons learned:
Continuous Monitoring Activities:
- Security Information and Event Management (SIEM): Collect and analyze security logs from various sources to identify potential threats.
- Vulnerability Scanning: Regularly scan your systems for vulnerabilities and apply patches.
- Penetration Testing: Periodically conduct penetration testing to identify weaknesses in your security posture.
- Security Audits: Conduct regular security audits to assess the effectiveness of your security controls.
- Incident Response: Develop and implement an incident response plan to address security incidents effectively.
- Reviewing Security Logs and Alerts: Actively monitor security logs and alerts for any suspicious activity.
Adapting to the Evolving Threat Landscape:
- Stay Informed: Keep abreast of the latest security threats and vulnerabilities through industry publications, threat intelligence feeds, and security conferences.
- Adapt Your Controls: Adjust your security controls as new threats emerge or as your organization’s operations change.
- Regular Review and Updates: Conduct regular reviews of your OPSEC strategy to ensure it remains relevant and effective.
- Employee Feedback: Encourage employees to report any security concerns or vulnerabilities they identify.
The Importance of Human Factors in OPSEC
While technology plays a significant role in OPSEC, human factors are equally critical. Employee training, awareness, and adherence to security protocols are essential for the success of any OPSEC program. Regular security awareness training should be a cornerstone of your OPSEC strategy.
Conclusion: OPSEC – A Never-Ending Journey
OPSEC is not a destination but a journey. It’s a continuous cycle of identifying, analyzing, controlling, and monitoring, constantly adapting to the evolving threat landscape. By embracing this cyclical approach, organizations can proactively mitigate risks, protect critical information, and maintain a strong security posture. Remember, a proactive, adaptable approach to OPSEC is not just about reacting to threats; it’s about anticipating and preventing them. This continuous cycle of improvement is what separates a robust OPSEC program from a reactive one. By integrating these stages into your organization's culture, you can build a robust and effective OPSEC program that safeguards your most valuable assets.
Latest Posts
Latest Posts
-
Business Letters Are Important For Any Transaction That Requires
Apr 05, 2025
-
Rewards Included In Health Action Plans Should
Apr 05, 2025
-
Which Of The Following Is Not A Type Of Inventory
Apr 05, 2025
-
Classify The Statements As True Or False
Apr 05, 2025
-
A Plastic Ocean Documentary Companion Questions
Apr 05, 2025
Related Post
Thank you for visiting our website which covers about Opsec Is A Cycle Used To Identify Analyze And Control . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
