Ncic Hosts Restricted Files And Non-restricted Files
Holbox
Mar 28, 2025 · 6 min read
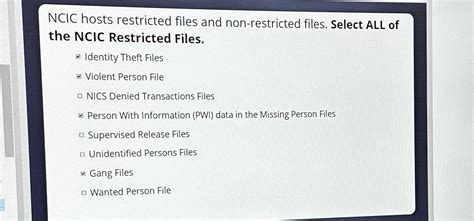
Table of Contents
- Ncic Hosts Restricted Files And Non-restricted Files
- Table of Contents
- NCIC Hosts Restricted Files and Non-Restricted Files: A Deep Dive into Data Security and Access
- Understanding the NCIC's Data Classification System
- Restricted Files: A Bastion of Sensitive Information
- Access Control for Restricted Files
- Non-Restricted Files: Publicly Accessible Information (With Limitations)
- Access Control for Non-Restricted Files
- The Importance of Data Security in the NCIC
- Future Trends in NCIC Security
- Conclusion: Balancing Accessibility and Security
- Latest Posts
- Latest Posts
- Related Post
NCIC Hosts Restricted Files and Non-Restricted Files: A Deep Dive into Data Security and Access
The National Crime Information Center (NCIC) is a vital database for law enforcement agencies across the United States. It houses an immense amount of sensitive information, requiring a robust and meticulously managed system to control access and maintain data integrity. This system relies heavily on a categorization of files as either restricted or non-restricted, a distinction crucial for both operational effectiveness and national security. Understanding this distinction, the implications of each classification, and the security measures implemented is key to appreciating the NCIC's role in maintaining public safety.
Understanding the NCIC's Data Classification System
The NCIC's data classification system is not publicly documented in its entirety. Information pertaining to specific access levels and the granular details of security protocols is naturally classified for obvious reasons. However, we can extrapolate a general understanding based on the types of information housed within the system and the known security procedures. The core principle is straightforward: information that could compromise investigations, endanger individuals, or compromise national security is designated as restricted. Conversely, data that poses minimal risk if accessed inappropriately is categorized as non-restricted.
Restricted Files: A Bastion of Sensitive Information
Restricted files within the NCIC contain information requiring the highest level of protection. This category encompasses a wide range of sensitive data, including:
-
Confidential Investigative Data: This includes details of ongoing investigations, including witness statements, informant information, and strategic plans. Unauthorized access could severely compromise the integrity of active investigations, potentially endangering lives and jeopardizing the success of operations.
-
Criminal History Records: While some aspects of criminal history are publicly accessible, detailed records often contain sensitive information, such as juvenile records, sealed records, or information related to ongoing legal proceedings. The unauthorized release of such data could have serious legal and personal consequences.
-
National Security Information: The NCIC may contain information related to national security, including intelligence gathered in relation to terrorism, organized crime, or other threats. Access to this information is strictly controlled, with authorization protocols in place to prevent leaks and ensure the protection of national interests.
-
Protected Personal Information: The NCIC houses Personally Identifiable Information (PII) of individuals involved in criminal activity, victims, and witnesses. Unauthorized access to this data could lead to identity theft, harassment, and other serious crimes. This includes sensitive data like social security numbers, addresses, and medical records.
-
Law Enforcement Tactical Data: This includes information related to law enforcement strategies, operational plans, and equipment deployment. Compromise of this data could significantly hinder law enforcement operations and increase the risk to officers.
Access Control for Restricted Files
Access to restricted files within the NCIC is controlled through a multi-layered security system. This typically includes:
-
Strict Authentication: Access is granted only to authorized users with proper credentials, typically involving multi-factor authentication procedures. This may involve biometric scans, password authentication, and smart card access.
-
Role-Based Access Control (RBAC): The system implements RBAC, which allows administrators to grant access based on the user's role and responsibilities. Different roles have different levels of access, ensuring that users only see the information necessary for their tasks.
-
Data Encryption: Sensitive data is encrypted both in transit and at rest, protecting it from unauthorized access even if the system is compromised. Strong encryption algorithms are employed to ensure the confidentiality of the data.
-
Auditing and Logging: All access attempts are logged and audited, creating a detailed trail that allows for investigation of any unauthorized access attempts or security breaches. This audit trail is essential for accountability and security compliance.
-
Regular Security Assessments: The NCIC system undergoes regular security assessments and penetration testing to identify vulnerabilities and ensure the system remains secure.
Non-Restricted Files: Publicly Accessible Information (With Limitations)
Non-restricted files within the NCIC represent a smaller portion of the database. While accessible with appropriate authorization, the definition of "non-restricted" still adheres to stringent data protection guidelines. This category typically includes:
-
Publicly Available Criminal History Information: This could include basic criminal history summaries that are permissible to release under relevant state and federal laws. However, even this information is subject to strict privacy regulations.
-
Statistical Data: Aggregated data used for crime analysis and reporting, stripped of personally identifying information. This type of data is essential for understanding crime trends and informing public safety policies.
-
Training Materials: Information used for training purposes within law enforcement agencies. This data is usually not considered sensitive, but access may still be restricted to authorized personnel.
Access Control for Non-Restricted Files
Access to non-restricted files is still controlled to prevent misuse and maintain data integrity. Although the level of security is lower than that applied to restricted files, the following measures are typically implemented:
-
Authentication: Users still need to authenticate their identities before accessing any NCIC data.
-
Access Logging: Access attempts are logged to track usage and detect any unusual patterns.
-
Data Validation: The system may have protocols in place to prevent unauthorized modifications or deletions of data, even within the non-restricted category.
The Importance of Data Security in the NCIC
The NCIC's robust security system is paramount for several reasons:
-
Maintaining Public Trust: Public trust in law enforcement relies on the responsible handling of sensitive data. Strict security measures are crucial for maintaining this trust.
-
Protecting National Security: The NCIC houses information crucial to national security. Breaches could have catastrophic consequences.
-
Preventing Identity Theft and Fraud: The database contains a vast amount of PII, making security essential to prevent identity theft and other forms of fraud.
-
Ensuring the Integrity of Investigations: Data breaches could compromise ongoing investigations, endangering lives and jeopardizing justice.
-
Upholding Legal and Ethical Standards: Strict security measures are vital to comply with data privacy laws and ethical guidelines.
Future Trends in NCIC Security
As technology continues to evolve, so too must the NCIC's security measures. Future trends likely include:
-
Enhanced Encryption: The adoption of even stronger encryption algorithms to protect against advanced cryptographic attacks.
-
Artificial Intelligence (AI) and Machine Learning (ML): The implementation of AI and ML to detect anomalous activity and prevent security breaches proactively.
-
Blockchain Technology: Exploring the potential of blockchain technology to enhance data immutability and transparency within the NCIC system.
-
Continuous Security Monitoring: Moving towards a more proactive and dynamic approach to security monitoring, enabling faster detection and response to threats.
-
Improved Collaboration and Information Sharing: Enhancing secure collaboration with other law enforcement agencies and intelligence organizations.
Conclusion: Balancing Accessibility and Security
The NCIC's distinction between restricted and non-restricted files reflects the delicate balance between the need for accessible information and the critical importance of data security. The system's multi-layered approach to access control is not merely a technical exercise; it is a fundamental aspect of maintaining public safety, protecting national security, and upholding the integrity of the criminal justice system. Continued investment in security technologies and practices is essential to ensure the NCIC remains a reliable and secure resource for law enforcement agencies across the nation. The ongoing evolution of these security protocols underscores the dynamic nature of cybersecurity and the constant need to adapt to emerging threats. The future of the NCIC's data security relies on the continuous refinement and modernization of its infrastructure and access protocols.
Latest Posts
Latest Posts
-
Moles And Chemical Formulas Report Sheet Answers
Apr 01, 2025
-
The Narrower The Definition Of A Product
Apr 01, 2025
-
Final Goods And Services Refer To
Apr 01, 2025
-
A Decrease In The Interest Rate Will
Apr 01, 2025
-
Which Statements Reflect A Servant Leadership Mindset
Apr 01, 2025
Related Post
Thank you for visiting our website which covers about Ncic Hosts Restricted Files And Non-restricted Files . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
