Assertions Are Checked After Database Modiication
Holbox
Mar 24, 2025 · 6 min read
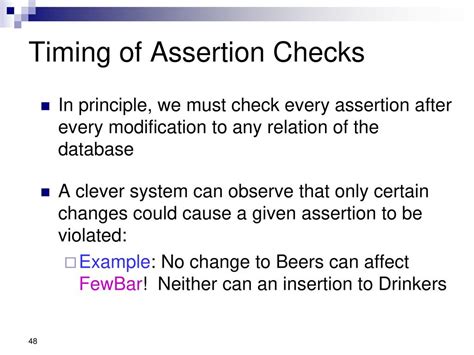
Table of Contents
- Assertions Are Checked After Database Modiication
- Table of Contents
- Assertions: The Unsung Heroes of Database Integrity After Modifications
- Understanding Assertions: The Guardians of Data Integrity
- Types of Assertions: Tailoring the Guard to Your Needs
- Implementing Assertions: A Practical Guide
- Beyond Basic Assertions: Advanced Techniques
- The Importance of Testing Assertions
- Assertions vs. Application-Level Validation
- Common Pitfalls and Best Practices
- Conclusion: Embracing Assertions for a Robust Database
- Latest Posts
- Latest Posts
- Related Post
Assertions: The Unsung Heroes of Database Integrity After Modifications
Database modifications are the lifeblood of any dynamic application. Whether it's adding a new customer, updating an order status, or deleting obsolete data, these changes are constant. However, maintaining data integrity after these modifications is crucial for the application's reliability and accuracy. This is where assertions come into play – silent sentinels guarding the sanctity of your database. This article dives deep into the world of assertions, exploring their role in ensuring data integrity post-modification and providing practical strategies for implementing them effectively.
Understanding Assertions: The Guardians of Data Integrity
Assertions are essentially declarative statements that specify conditions that must always be true for your database. They're like rules embedded within your database schema, constantly validating the state of your data. If an assertion is violated, the database rejects the modification, preventing corrupted or inconsistent data from entering the system. This proactive approach to error handling is far superior to reactive methods that only detect problems after they've already occurred.
Types of Assertions: Tailoring the Guard to Your Needs
Different database management systems (DBMS) offer various types of assertions, each suited for specific scenarios:
-
Check Constraints: These are the most common type, enforcing conditions on individual rows within a table. For example, you might use a check constraint to ensure that the
agecolumn in aCustomerstable is always greater than or equal to zero. -
Table Constraints: These constraints apply to an entire table and often relate to multiple columns. They can be particularly useful for enforcing relationships between different tables or more complex business rules.
-
Domain Constraints: These constraints define allowed values for specific data types. For example, you could define a domain to restrict the values in a
statuscolumn to a predefined set ("active," "inactive," "pending"). -
Foreign Key Constraints: These are essential for relational database integrity, ensuring that foreign keys in one table refer to valid primary keys in another table, thereby maintaining referential integrity. Violating this constraint would prevent actions like deleting a record referenced by foreign keys.
-
Triggers: Although not strictly assertions, triggers provide a procedural mechanism for enforcing data integrity. They execute automatically before or after database modifications, allowing you to perform checks and potentially rollback transactions if conditions aren't met.
Implementing Assertions: A Practical Guide
The specific implementation of assertions varies across different database systems (e.g., MySQL, PostgreSQL, Oracle, SQL Server). However, the underlying principles remain consistent. Let's consider some examples:
Example 1: Check Constraint for Age in a Customers Table (SQL):
ALTER TABLE Customers
ADD CONSTRAINT CK_CustomerAge CHECK (Age >= 0);
This constraint ensures that no customer can have a negative age. Any attempt to insert or update a customer record with a negative age will result in a database error.
Example 2: Table Constraint for Inventory Levels (SQL):
Imagine you have an Inventory table with product_id, quantity, and reorder_level columns. You want to ensure that the quantity never falls below reorder_level.
ALTER TABLE Inventory
ADD CONSTRAINT CK_InventoryLevel CHECK (quantity >= reorder_level);
This constraint enforces the business rule of automatically triggering a reorder when inventory falls below a specified threshold.
Example 3: Trigger to Enforce Audit Logging (PL/SQL - Oracle):
This example shows a more complex scenario where a trigger logs all modifications to a table:
CREATE OR REPLACE TRIGGER TRG_CustomerUpdate
BEFORE UPDATE ON Customers
FOR EACH ROW
BEGIN
INSERT INTO AuditLog (table_name, action, old_data, new_data)
VALUES ('Customers', 'UPDATE', :OLD, :NEW);
END;
/
This trigger intercepts any update to the Customers table and automatically logs the changes in the AuditLog table. While not a direct assertion, it ensures data integrity by providing a complete audit trail for all modifications.
Beyond Basic Assertions: Advanced Techniques
The power of assertions extends beyond simple constraints. They can be leveraged to implement sophisticated business rules and data validation logic:
-
Combining Multiple Conditions: Assertions can include multiple conditions using logical operators (AND, OR, NOT) to create complex validation rules.
-
Using User-Defined Functions: You can incorporate user-defined functions within your assertions to perform complex calculations or checks, making them more versatile and adaptable.
-
Cascading Assertions: Assertions can be strategically layered to create a robust system of checks and balances, ensuring that data integrity is upheld across multiple tables and relationships.
The Importance of Testing Assertions
Thorough testing is crucial to ensure that assertions are functioning correctly and catching potential violations. This involves:
-
Unit Testing: Individual assertions should be tested independently to verify their behavior under various conditions.
-
Integration Testing: Assertions should be tested in conjunction with other parts of the database and application to identify any unintended side effects or interactions.
-
Stress Testing: Testing under high-load conditions can help identify performance bottlenecks or limitations of your assertions.
-
Regression Testing: After database schema changes or code updates, regression tests must be conducted to ensure that assertions still function as expected and do not inadvertently break any existing functionality.
Assertions vs. Application-Level Validation
While assertions provide crucial database-level integrity checks, they shouldn't replace application-level validation. Application-level validation acts as the first line of defense, preventing invalid data from even reaching the database. Assertions serve as a backup, catching any data that might slip through application-level checks due to bugs or vulnerabilities. This layered approach creates a robust system for maintaining data integrity.
Common Pitfalls and Best Practices
-
Overly Complex Assertions: Avoid creating overly complex assertions that are difficult to understand and maintain. Break down complex logic into smaller, more manageable components.
-
Performance Considerations: Complex assertions can impact database performance. Optimize your assertions to minimize their overhead and avoid unnecessary computations.
-
Error Handling: When an assertion fails, handle the error gracefully. Provide informative error messages to help identify the root cause of the problem.
-
Regular Review and Maintenance: Regularly review and maintain your assertions to ensure they remain relevant and accurate. Outdated assertions can become a liability rather than an asset.
Conclusion: Embracing Assertions for a Robust Database
Assertions are an invaluable tool for ensuring data integrity in any database-driven application. By actively enforcing business rules and data validation constraints at the database level, you create a more reliable, resilient, and trustworthy system. While implementing assertions requires careful planning and testing, the long-term benefits far outweigh the initial investment. Through a combination of strategically placed assertions, robust application-level validation, and a diligent testing regimen, you can significantly enhance the quality and integrity of your data, ultimately leading to a more robust and successful application. Remember that a well-structured approach, encompassing both application-level validation and database-level assertions, is the best way to ensure complete data integrity. Don't rely solely on one; use them both in conjunction for maximum protection. The time spent carefully crafting and testing your assertions is an investment in the long-term health and reliability of your database.
Latest Posts
Latest Posts
-
If A Management Team Wishes To Boost
Mar 29, 2025
-
Working In A Comfortable Environment With Enough Heat And Air
Mar 29, 2025
-
Connections Between Two Threaded Faucets Should Have An Approved
Mar 29, 2025
-
What Is The Difference Between Technology And Technological Change
Mar 29, 2025
-
Eurail And Swiss Rail Are Hypothetical Railways
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about Assertions Are Checked After Database Modiication . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
